Section 1:
Market Overview
Key Points
- Security is becoming the top IT priority for companies, as the recent history with new technology models and the reliance on data has brought focus to the need for tight security and privacy. Accordingly, the market is growing, with Gartner projecting overall spending on enterprise security to reach $100.3 billion globally by 2019.
- Three different movements are driving the modern security approach: the shift away from the secure perimeter, the balancing of prevention and detection, and the increased focus on proactive security activities. Businesses must combine technology, processes, and education in order to properly protect their digital assets.
- Security workforce issues are split into two parts. Core technical skills are in high demand, with BLS data showing that the number of job postings in the classification “Information Security Analysts” rose 48% between Q4 2014 and Q4 2015. Separately, companies must consider how to train the general workforce, as the average use of technology has outpaced average security literacy.
The Rise of Security
The past several years have seen dramatic shifts in enterprise technology. Companies have moved past early experiments with cloud systems to adopt a cloud-first mentality when planning infrastructure. Mobile devices have become ubiquitous, extending the personal computing platform and increasing productivity and efficiency. Digital data has grown in relevance as businesses collect data from new sources and extract new insights.
Yet for all the focus on cloud, mobility, and big data, a more traditional topic is quickly becoming the top priority in the IT industry. Cybersecurity has been a concern for businesses ever since they started building digital assets, but new technology models along with a greater reliance on that technology are driving changes in how companies approach security, resulting in a field rich with opportunity.
Sizing Security Market Segments
Market sizings are notoriously abstract, with different firms using different definitions for various markets and business conditions constantly changing estimates. For a broad field like security, sizings are especially elusive. Still, the projections give some shape to the overall market and some of the major components.
Gartner reports that overall enterprise security spending hit $75.4 billion in 2015. They project that the market will grow at 7.4% CAGR through 2019, resulting in revenue of $100.3 billion.
The cloud security market—meaning the application of security to assets residing in the cloud—reached $5.1 billion in 2015, according to Transparency Market Research. They call for 12.8% CAGR through 2019, resulting in revenue of $8.2 billion.
Mobility has a stronger consumer side than cloud computing, but focusing on just enterprise mobility, MarketsandMarkets estimates that $1.97 billion was spent in 2015. They expect even more robust growth than the cloud security market will experience, with 30.7% CAGR leading to $5.8 billion in revenue by 2019.
Each new technology model comes with its own specialized security issues. In the early days of cloud computing, security was commonly cited as a barrier to adoption. Over time, companies have resolved their concerns adequately enough to begin experimentation or migration, but this does not signal that cloud security has been solved. Cloud providers commonly take the position that they secure their infrastructure, leaving security of data and applications to the client. Clients may benefit from a cloud provider’s excellent infrastructure security, but they still need to determine their desired security profile and close any gaps between the cloud provider and their ideal outcome.
Mobile security naturally started with a focus on devices as smartphones and tablets charged onto the business landscape. IT departments and solution providers had some experience with mobility thanks to laptops and Blackberry phones, but these devices were designed to be enterprise-grade. Consumer-grade devices presented brand new challenges. As companies made decisions on BYOD and MDM, they realized that devices were only the first new piece in the modern mobile ecosystem. The nature of software has changed with the app model, and there are network considerations as public Wi-Fi has proliferated and cellular networks are robust enough for productive work.
As companies transform into digital organizations, their data becomes a critical resource. Businesses are making great strides towards managing their data better and effectively using data to improve business operations. Better data security is a big part of better data handling. With data now traveling regularly outside a company’s secure perimeter, the data itself needs to be monitored and analyzed. In addition, data privacy is becoming a concern separate from security as customers also try to ensure that their data is being handled appropriately.
All of these new technology trends carry security implications, and one of the huge challenges moving forward is folding these new implications into existing security practices that may require improvements of their own. The major security breaches over the past several years from Target, Home Depot, Anthem, and others have highlighted the growing importance of technology, but most of them have not involved mistakes using cutting edge models. Instead, they have been caused by failure to follow established best practices or attacks of a more traditional nature. New models will simply exacerbate the problem as criminals and bad actors learn how to exploit them. Keeping company assets safe will require a new mindset around cybersecurity.
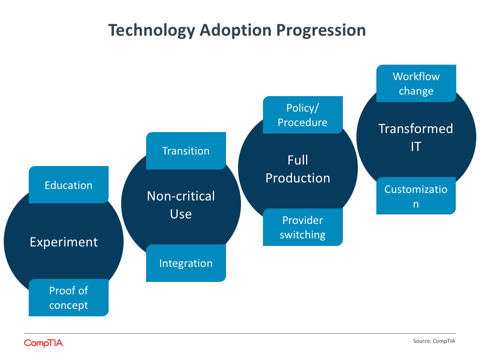
Taking a New View
Extensive changes in IT operations, increased reliance on technology, and heightened awareness around breaches have all led to an evolution in the corporate security approach. What was once an isolated function within the IT department is now a broader initiative, driven by three primary shifts in the way companies think about building a secure posture.
First, the notion of a secure perimeter has mostly vanished. Companies may still create secure zones to hold their most prized information, but for the most part they must contend with data and applications running in cloud providers and on mobile devices. The technology adoption progression that CompTIA has defined ends with Transformed IT, where the overall infrastructure has been re-architectured to take advantage of new models. Building security into data and applications is part of this effort.
The shift away from a secure perimeter begins as a technology discussion, where standard security tools such as firewall and antivirus are supplemented with new tools such as Data Loss Prevention (DLP) and Identity and Access Management (IAM). However, the discussion quickly broadens. Businesses must add new processes, such as risk analysis, compliance management, and cloud provider evaluation. In addition, businesses must consider how to educate end users who have become the weakest link in the chain as their technology skills outpace their security knowledge.
Unfortunately, all of these measures only lessen the chance of a breach in today’s environment, not remove it altogether. The second shift, then, is towards less prevention and more detection. Leading security practitioners now place a high priority on the ability to find anomalous behavior in an application or a network and quickly resolve the situation.
Looking at Layered Security
Layered security is not a new topic, but it is one that is getting more focus as a wider range of tools are being used by companies to create a secure posture. The basic notion of layered security is to combine a variety of tools and practices to catch different types of threats or to isolate different parts of a system. In a simple form, think of multiple firewalls creating different zones for network traffic to pass through, allowing for multiple levels of analysis. Most layered security implementations are significantly more complex, leading to the major challenges with the practice. A complex configuration requires a high degree of maintenance, especially in a constantly-changing field like security. Even with the proper configuration, organizations must know how to properly respond when a problem is discovered. This highlights the three-pronged approach required for modern security: technology, process, and education.
Again, part of the solution is technical. One of the more robust segments of the security software market is Intrusion Detection Systems/Intrusion Prevention Systems (IDS/IPS). MarketsandMarkets predicts that this field will grow at a Compound Annual Growth Rate (CAGR) of 13.2% between 2014 and 2019, placing it behind fields such as DLP (22.3%) and IAM (14.9%), but ahead of firewall (6.5%) and endpoint security (8.4%).
The final shift adds to the thinking that breaches are inevitable, as companies move from a defensive stance on security to an offensive strategy. In part, an offensive strategy builds on the second shift towards detection, as companies proactively audit and test their own infrastructure and security solutions in order to find possible faults. The offensive strategy also helps mitigate risk in the event a breach does occur; it will be increasingly prudent for a company to demonstrate due diligence in order to protect their reputation.
Clearly, security is no longer a discipline confined within a single department. Businesses still look to the IT function to direct overall security activities, but those activities involve discussions and processes that happen throughout the organization. In order to successfully implement a new security approach, companies must consider the skills that they need to build or bring in.
Workforce Issues
The wide array of technical skills needed for security and the difficult task of educating the general workforce both contribute to a complex picture for companies trying to build a security team. Adding to the complexity, companies have different approaches to the IT function, using a mix of internal resources and third party expertise.
At the top end of the scale, security is becoming its own function. Many large corporations are creating the role of Chief Information Security Officer (CISO) or Chief Security Officer (CSO), and some companies have explored organizational restructuring with these roles. In some cases, the CISO continues to report to the CIO (or possibly the COO). Other companies have the CISO report directly to the CEO, giving broader organizational reach and integration. Booz Allen has actually taken this a step further and reversed the traditional arrangement so that the CIO reports to the CISO. With its recent cybersecurity budget including a provision for a federal CISO, the U.S. government is one of the highest profile organizations to demonstrate the need for a specific security focus.
At the other end of the scale, companies with no formal IT function have major challenges in bringing dedicated security skills on-board. As they commonly use outside firms for IT activities, they will naturally turn to these firms for security activities as well. The IT channel has seen a rise in managed security service providers (MSSPs), where the entire portfolio of products and services is built around security. Of course, working with such a firm adds to the list of partners a company must employ, but the complexity of security and of IT overall is making a jack-of-all-trades partner a difficult proposition.
The net effect of all this churn is a rapidly increasing demand for security skills. According to BLS data from January 2016, the number of job postings in the classification “Information Security Analysts” rose 48% between Q4 2014 and Q4 2015. This was the second-highest rate of growth across all BLS IT classifications, trailing only “Computer & Information Research Scientists.”
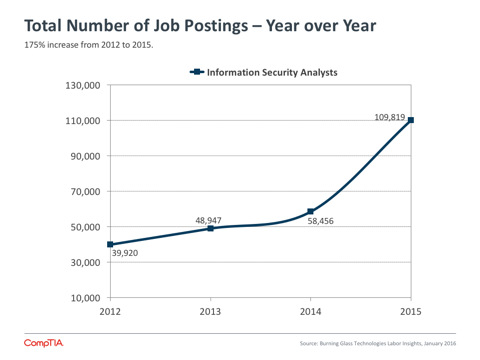
Job postings are a proxy for true job demand, given that hiring firms may change their plans, post multiple times for the same job, hire internally, or try different approaches to find the right candidate. The strong growth in the Information Security Analysts category matches with anecdotal evidence that companies are seeking a variety of technical skills, from firewall administration to intrusion detection to the use of data analytics to target potential security threats.
Beyond security-specific roles, companies are expecting security to be a larger part of general technical positions along with non-technical functions. CompTIA’s Security+ certification also experienced growth of 18% between Q4 2014 and Q4 2015. While this certification is often used as the first step towards an InfoSec career, the vendor-neutral approach provides a solid foundation in security for professionals pursuing paths such as cloud architecture or data science.
For the general workforce, companies are exploring ways to raise security literacy and mitigate the risk of human error. Educational offerings delivered via an online classroom are a good first step and hold the potential to factor into the cost of cyberinsurance. Going further, some companies are using more novel approaches such as simulated phishing attacks or gamification to measure and improve awareness.
Security is on the rise, but not because companies are suddenly recognizing the importance of protecting their assets. Businesses with serious IT investments have always viewed security as a high priority, but the stakes are now higher. With the changes happening in enterprise technology, digital organizations have a lower tolerance for data breaches or infrastructure attacks. With the changing motivations of cybercriminals, companies of all sizes must be more vigilant about their data and the data of their customers. Both IT departments and solutions providers will need to build new tools, skills, and behaviors as they maintain corporate security in the modern technology era.
Section 2:
Business Model Analysis
Key Points
- Many channel firms claim to have robust security portfolios, offering a wide mix of technologies and services. However, factors such as broad vendor features or lack of customer demand could drive channel firms to claim a specific technology or service without necessarily having the wherewithal for immediate implementation.
- Looking at the technologies and services that generate the most volume or revenue, there is more demarcation among channel offerings. Overall, 38% of companies say that firewall is their biggest seller, followed by 20% that place antivirus at the top. The next highest item is SIEM, coming in at just 9%.
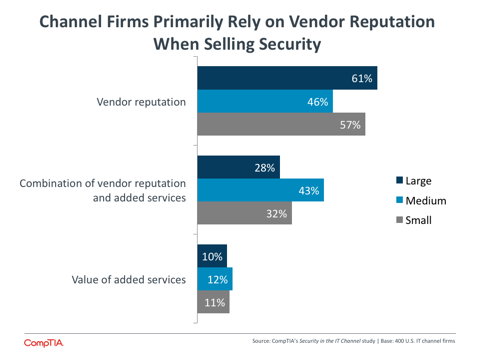
- The historical model of reselling vendor products has carried over into the way channel firms present themselves. The majority of partners still rely on the the strength of vendor products and branding when selling to clients, with just 1 in 10 primarily focusing on their own services or value-add proposition.
Channel Security Portfolios
Today’s channel firms face several choices. Which vendors are offering products that meet the needs of digital organizations? Does it make sense to focus on a specific vertical? What is the ideal mix of product-based work and services? Chief among these choices may be the decision on which business model to pursue and the breadth of offerings that will be made available.
Although small businesses may not be fully prepared to engage with a wide array of partners, the growing complexity of IT environments makes it increasingly difficult for a single firm to provide expertise in all areas. Many channel firms gravitate towards a defined domain, whether that is a function they have built up over the years or a new field utilizing new trends in technology.
Security on its own has many different aspects, but a channel firm with the right resources can serve as the InfoSec team for businesses that need assistance. With comprehensive security moving beyond simple product installation and turning into an ongoing process, the channel firms stepping into this space are typically either managed service providers with a primary focus on security or companies that adopt security as their sole line of business and label themselves managed security service providers. CompTIA focused on these two groups for the Security in the IT Channel study in order to determine which products, services, and behaviors are most applicable in today’s climate.
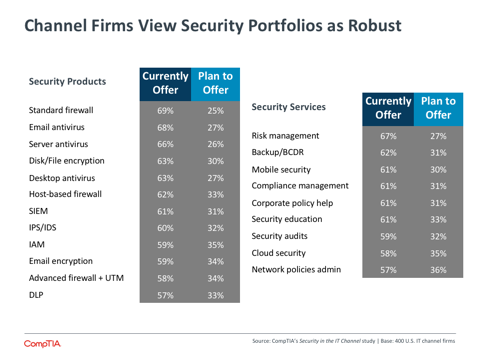
From an offering standpoint, the data suggests that these firms have very broad portfolios. The majority of security-focused firms currently offer each of the specific technologies in the above chart, which were drawn from the IT Security Wizard developed by CompTIA’s Security Community. Likewise, most firms claim to offer security services, which may involve multiple technologies or management of business processes.
However, it is worthwhile to consider exactly how “offering” is defined. Several factors could drive channel firms to claim a specific technology or service without necessarily having the wherewithal for immediate implementation. First, many vendors do offer a wide range of products, and a channel partner may assume that they can readily support a new product, even if they currently only support a small subset.
Along the same lines, channel firms may have researched certain tools or procedures but not actually have active customer engagements. Of course, a solution provider might view this as a function of their customer base. If clients aren’t asking for certain products or services, the SP may feel that they have offerings in the portfolio that are simply dormant, waiting for the first opportunity to go live.
Where the Money is Made
Overall ranking of security technologies/offerings when respondents were asked to highlight top three in terms of volume/revenue:
Standard firewall
Host-based firewall
Advanced firewall + UTM
Email antivirus
SIEM
DLP
Desktop antivirus
Server antivirus
Disk/file encryption
IPS/IDS
Cloud security
Corporate policy work
Email encryption
Risk management
Network policy management
Backup/BCDR
IAM
Mobile security
Security audits
Security education
Compliance management
Finally, there is the possibility that channel firms are not fully educated on various products or tools and believe that an offering exists where one does not. This is not a particularly generous explanation, but it is one that has some recent historical backing. As definitions of new trends have been debated, the IT industry in general has been quick to apply labels. Cloud-washing is a well-known example of this. The term has faded somewhat as an exact cloud definition is not critical for many use cases, but vendors and partners have applied “cloud” to products and services without specifying the defining characteristics. Definitions become important when specific functions are required, and discussion about various security tools fits that scenario. Having a given tool in the portfolio implies solid knowledge of the tool and its function.
With these variables in mind, further data from the study shows that security portfolios are more limited in practice. To start, the rank order of the technologies offered is in line with expectations, with firewall and antivirus dominating the top half of the list and more advanced technologies appearing lower.
This trend continues when companies list which security offerings have the most volume and revenue. Again, firewall and antivirus lead the pack, with SIEM and DLP also relatively high on the list. This ranking also shows a significant divide between technologies and services. All security services are in the bottom half of the list, showing that even firms that are managing security on a recurring basis are primarily focusing on monitoring and management at a technical level.
Looking at those items that companies rank at the top in terms of volume/revenue sheds even more light on the situation. Overall, 38% of companies say that firewall is their biggest seller, followed by 20% that place antivirus at the top. The next highest item is SIEM, coming in at just 9%.
For the top two categories, there is an interesting division according to company size. Firewall is the top seller at 44% of large companies (50+ employees) and 40% of medium-sized companies (20-49 employees), but just 26% of small companies (1-19 employees). Conversely, 27% of small companies say that antivirus is their best seller, compared to 19% of medium-sized companies and 15% of large companies).
The problem is one of complexity and resource. Installing a firewall on the network, understanding different types of traffic or application behavior, and appropriately configuring policies is a more complicated task than installing an antivirus package on an endpoint device. Obviously antivirus management can be elaborate as well, but there is a definite gap between the two technologies in terms of minimum viable product.
This dynamic persists throughout the range of technology options, and in fact grows more dramatic as more technology options are brought to bear on a single customer solution. With multiple technologies working in concert, the challenge becomes the interaction between different tools and the required responses to events. A modern security approach does require a broad mix of products and services, and channel firms should be sure that they can support this mix beyond simply stating that items are available for purchase.
Building the Brand
The weighting of technology products over services leads to another issue for channel firms focusing on security: the tools they use when presenting themselves to clients. While MSPs and younger firms are leading the charge to focus more on individual brand, channel partners still overwhelmingly rely on the reputation and strength of vendor products when making sales. Approximately one-third of all firms balance vendor reputation and value-added services in their messaging, with only 1 in 10 primarily relying on the strength of their own services or innovation.
Medium-sized firms are the most likely to be emphasizing the unique attributes they bring to the table. These businesses have enough operational resource to focus on marketing activities, and they are the most likely to be searching for organic growth using innovative models. Smaller firms lack the resources to investigate new service approaches or market specific skills, and larger firms (of which there are few) typically have a franchise model where vendor brand is a way of building consistency.
Marketing certainly plays a role in the shift towards value-added services as the primary sales tool. CompTIA’s 4th Annual State of the Channel study examined the challenges that channel firms face in expanding their marketing activities. Older firms are less likely to be planning changes to their sales and marketing strategy, having built strong practices around the vendor products they support. Younger firms, especially those in business less than 4 years, are pursuing techniques such as social media, white labeling, and webinars in order to promote themselves.
Good marketing still requires a solid product. For channel security firms to successfully build their brand with their customer base, they must find the unique strengths that they can use to solve problems. With software playing a much larger role in defining the IT experience, many firms are exploring some flavor of development to extend product functionality or provide monitoring capabilities.
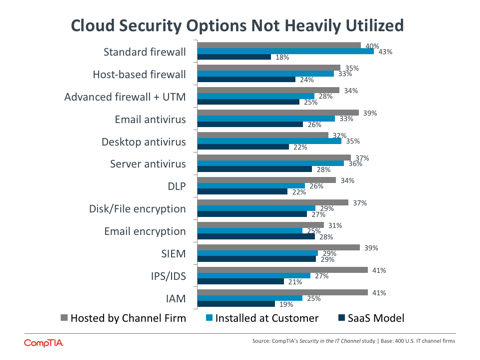
For most firms, though, software development is a new field with a steep learning curve. A more natural place to begin building differentiation would be lower in the IT stack, at the hardware infrastructure level. Since the focus is currently on technology components, solution providers should consider where those components are installed.
Many channel firms have taken a step in this direction by hosting security applications on their own infrastructure rather than at the client site. However, this trend has not yet carried over into the cloud world, with SaaS applications the least popular option for each technology, often by a wide margin. In addition to exploring SaaS models more thoroughly, solution providers should also explore hosting applications in cloud infrastructure. By utilizing cloud components to a greater extent, providers can reduce the effort spent in infrastructure maintenance and concentrate more on delivery and integration of the final security methodology.
Technology remains a critical part of a security approach, even as secure perimeters are relegated to minor elements of a defense. As channel companies pursue security as a specialization, they must focus more on the higher-level services that drive comprehensive monitoring and response, and they must find ways to build their own brand by adding value to the vendor products that are utilized.
Section 3:
Workforce Perspectives
Key Points
- Although modern security is a complex field covering many disciplines, channel firms generally feel that they have the skills they need in-house to address their current security activities. Forty-two percent of companies feel that they have some level of skill gaps, with just 4% believing that major gaps exist today.
- To close skill gaps, companies have taken several different approaches. The most popular is training, especially among small channel businesses where 85% have trained in order to build skills. Partnering is another strong option, showing that the many discussions about providers partnering with each other may be starting to bear fruit. The least common option is hiring, though this happens far more at medium-sized firms than small or large companies.
- There is an even split when it comes to initiating security discussions—channel firms start the conversation 51% of the time, and clients open up the dialogue 49% of the time. Channel firms should be sure to focus on the cost of poor security, especially as more discussions include CEOs and lines of business.
Finding the Right Skills
As with several rapidly growing areas in technology, security is a field where companies are starting to run into a supply and demand problem with qualified workers. Especially with accelerating interest in protecting digital assets and reputation, businesses are searching for the skills they need across the broad range of security topics.
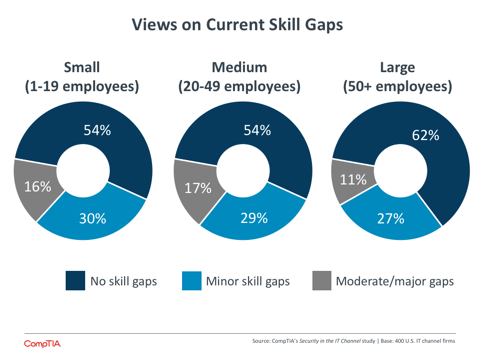
Channel firms generally feel that they have the skills they need in-house to address their current security activities. The data is relatively consistent across company size, with a slight difference showing up for moderate skill gaps. Fifteen percent of medium-sized firms report moderate skill gaps, compared to 9% of small firms and 8% of large companies.
The fact that most channel firms feel that their skills are sufficient for current needs is another signal that they may not fully support the wide range of security offerings described in Section 2. Companies with fewer than 50 employees are not likely to have deep expertise across all security technologies along with compliance proficiency and skills in educating end users. Instead, the skills are likely grouped around a select few areas, with passing knowledge of other subjects.
For those businesses that recognize some level of skill gap, there is also recognition that security spans several different disciplines. Again, there is a weighting towards the technical side of things: 58% of companies with gaps say they would like to improve knowledge of current security technologies, and 58% say they would like to improve knowledge of security threats. However, there is strong demand for other areas as well, with 47% saying they would like to gain skills in dealing with end users and 46% saying they would like to improve awareness of the regulatory environment.
Section 1 covered the sharp increase in security job postings, reflecting a high demand for enterprise security skills. It comes as no surprise that the skill supply is struggling to keep pace. As security pushes into new topical areas, there is not an established core of available workers with the skills and mindset to address modern challenges.
Cloud computing has created cloud architects, big data has created data scientists, and security also has its own new role that illustrates the shifting landscape. As businesses take a more proactive approach to ensure a strong position, security analysts will feature more prominently. This position will use data gathered from network, application, and device usage to model typical behavior within the organization. That model can then be used to determine any anomalies in the system or to predict the most likely vectors for future attacks.
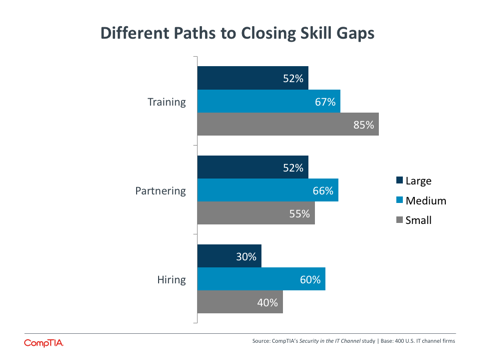
Whether pursuing advanced skills like security analysts or more traditional skills like firewall configuration, the scarcity of available talent makes hiring the least common choice for companies trying to close skill gaps. Only 42% of all businesses with skill gaps have hired recently, while 57% have turned to partnering with other channel firms and 68% have employed training.
Medium-sized firms are most aggressive in both partnering and hiring. With these firms being the ones most likely to report moderate skill gaps, they probably have a good sense of the specific proficiencies they are searching for as they try to provide comprehensive solutions. Smaller firms, with less resource to bring in new hires or search out viable partners, lean more towards training as an avenue for improved the skills of their workforce.
Engaging with Clients
The skills required for building security solutions are not the only ones that channel firms need to bolster. As technology decisions are being made throughout end user organizations, security issues are not fully understood even if the topic is a high priority. Selling security is becoming a critical activity, often requiring a more proactive approach and a broader set of discussions than in the past.
The balance seen in the way security discussions get started shows that channel firms are taking steps towards proactive selling, especially with clients that may not appreciate the characteristics of today’s digital economy. Fifty-one percent of channel firms say that they initiate security discussions with their customers, which tracks well with the 44% of customers that are assessed as having less than a very high level of urgency towards security matters. For these customers who are likely not aggressive in pursuing their own improvements, a conversation about today’s security landscape and the available methods can help raise awareness.
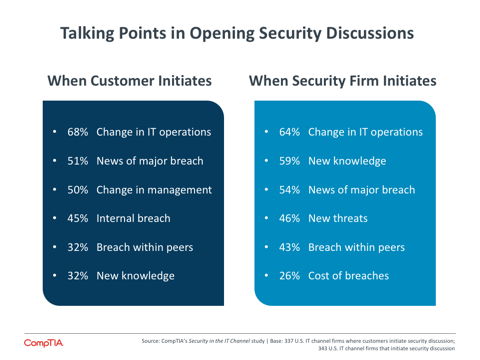
The primary talking point, regardless of who opens the security discussion, is a change in IT operations. This is a continuation of a positive trend seen in previous CompTIA research: rather than relying on security being a high priority to drive investment, a specific conversation around new IT models that have been put in place can drive conversation around appropriate security steps that should be taken.
The difference between the two sides when it comes to new knowledge gained through training or research highlights the value that a technology firm can bring. Many clients do not have the resources or bandwidth to seek out new technical knowledge. They rely on their solution provider to be their advisor, bringing in ideas and suggestions to drive growth or improve defenses.
Breaches obviously drive a great deal of discussion, whether they are major breaches that make headlines, internal breaches that push a client into action, or breaches at client peers that suggest best practices should be followed. However, the cost of breaches is an area that channel firms should focus on more in their sales. The 2015 Cost of Data Breach Study conducted by IBM and Ponemon Institute found that the average total cost of a data breach has increased 23% over the past two years, now reaching $3.79 million.
Smaller companies may feel that this data is heavily influenced by large organization that experience massive breaches. While the costs may accumulate quickly in the event of an enterprise-level breach with millions of records, the average cost for each lost or stolen record can still cause headaches at the SMB level. This cost, reaching as high as $165 in the retail sector, includes the investment in time and energy required to restore the data along with the steps that must be taken to repair any damage to reputation.
The study finds that one crucial step to mitigate risk and lower cost is executive involvement in security strategies. This is another thing for security firms to keep in mind as they have discussions with their clients. While the CEO or owner is typically getting involved in security discussions, there is far less involvement among other business units. This is somewhat to be expected at smaller firms that may not have well-defined business units, but even channel firms with large clients of 500+ employees see low engagement here.
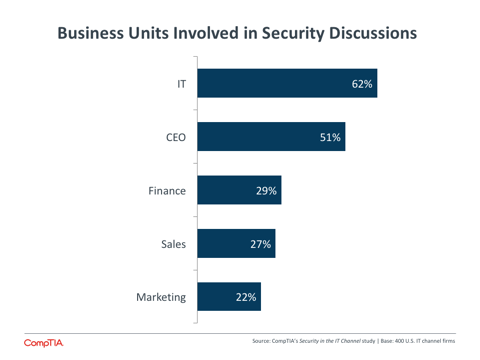
This is in line with other data on line-of-business technology procurement that CompTIA has gathered. In general, the tendency of business units to drive their own technology without involving the IT department—also known as rogue IT—is in decline. However, one of the major issues caused when this does happen is a misstep in security. It is no surprise to see that finance, sales, and marketing are less involved in security discussions even though they may be more involved in general technology decisions.
Having IT lead the way in security discussions may be a remnant of past behavior, but it also signals a trend taking place within burgeoning digital organizations. While all leaders are coming to the table for technology decisions, there are still some responsibilities that IT is expected to own. Security is one of these. Technical literacy throughout an organization has improved, which allows broader decision-making to take place. But security literacy is still low in most departments. The IT function within an organization, which may be filled completely or partially by a solution provider, has the security expertise necessary to keep a company safe, and they should be driving broad conversations that lead into new security strategies.
About this Research
CompTIA’s Security in the IT Channel study examines the practices of channel firms focusing on security as a primary or exclusive line of business.
The study consists of three sections, which can be viewed independently or together as chapters of a comprehensive report.
Section 1: Market Overview
Section 2: Business Model Analysis
Section 3: Workforce Perspectives
The data for this quantitative study was collected via an online survey conducted during January/February 2016. A total of 400 professionals within the IT channel participated in the survey, yielding an overall margin of sampling error at 95% confidence of +/- 5.0 percentage points. Sampling error is larger for subgroups of the data.
As with any survey, sampling error is only one source of possible error. While non-‐sampling error cannot be accurately calculated, precautionary steps were taken in all phases of the survey design, collection and processing of the data to minimize its influence.
CompTIA is responsible for all content and analysis. Any questions regarding the study should be directed to CompTIA Research and Market Intelligence staff at [email protected].
CompTIA is a member of the Market Research Association (MRA) and adheres to the MRA’s Code of Market Research Ethics and Standards.
Read more about Industry Trends, Cybersecurity.

 Download Full PDF
Download Full PDF