Cybersecurity is a constant balancing act. For years, the tug-of-war has been framed as a contest between security and convenience. Today, a new challenge is emerging.
The conflict is not so much with convenience as it is with progress. As organizations go through digital transformation and tie technology initiatives tighter to business success, excessive cybersecurity efforts can hinder overall progress. CompTIA’s 2024 State of Cybersecurity report explores the many variables that must be considered in balancing the cybersecurity equation.

Market Overview: The Current State
The simplest way to describe both the corporate stakes for cybersecurity and the challenges involved in crafting cybersecurity policy is to say that the scale has grown dramatically.
- From a threat landscape perspective, companies can see that the number of cybercriminals is skyrocketing, their organizational ability is growing and the potential damage from a cyberattack can be catastrophic.
- From an information security perspective, there is far more data being captured, with both privacy implications for customers and operational risk for internal workflows.
- From a product perspective, generative artificial intelligence (AI) is accelerating capabilities, often making the skill gaps at organizations even wider.
Our approach to defending cyberspace is changing – and we’re starting to see these changes having an effect:
- In 2022, only 25% of survey respondents felt that the overall state of cybersecurity in the economy was improving dramatically. In 2023, that number increased to 27%.
- In 2022, only 24% of respondents said their organization’s cybersecurity was completely satisfactory. In 2023, that number grew to 28%.
But information technology (IT) staff and cybersecurity professionals have a different perspective than executive stakeholders:
- More than 4 in 10 executives report being completely satisfied.
- But just 25% of IT staff and 21% of business staff share that sentiment.
Even with small gains in satisfaction, there is still plenty of room for improvement. The next stage of maturity involves establishing and refining cybersecurity operations, using strategic policy and processes to drive tactical actions around people and products.
Policy: Risk Management Is the Driving Force Behind Cybersecurity
Risk management is becoming the primary method for solving one of our greatest challenges: The connection between cybersecurity strategy and business operations.
When cybersecurity professionals:
- Identify various risks
- Assign the probability of cyber incidents
- Determine potential cost
- Propose incident response plans
The link between cybersecurity spending and desired outcomes gets stronger.
Do You Need a Formal Risk Management Framework? See what our respondents are doing:
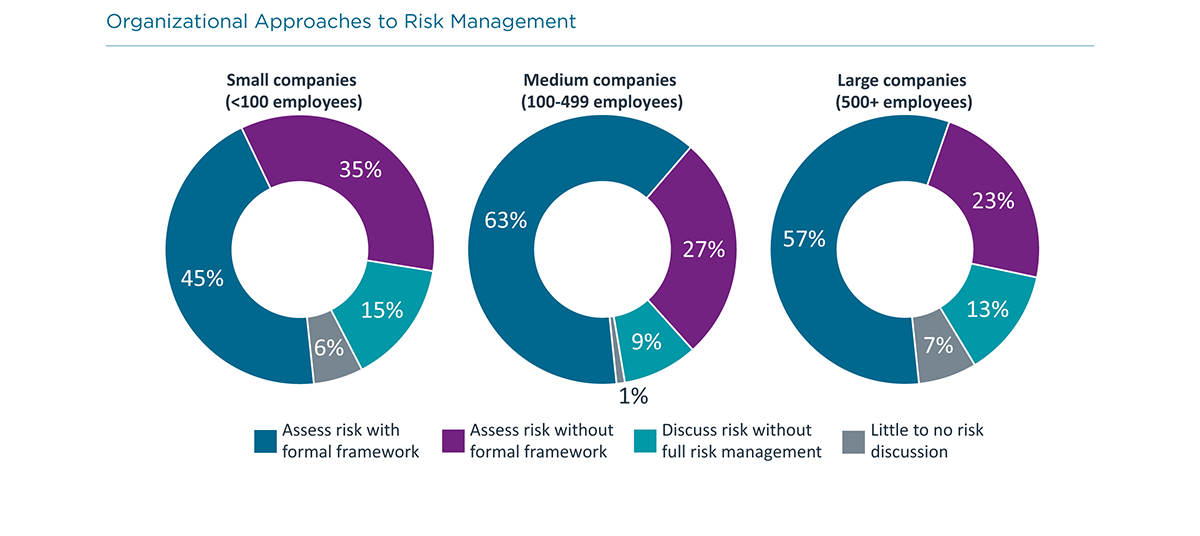
One of the best reasons to use a formal framework is to help identify areas that may lie outside traditional IT system architecture.

Beyond technical topics, thorough risk analysis also examines policies and processes that may have little to do with the IT team.
Process: Cybersecurity Processes Drive a Wide Range of Decision-Making
Following a comprehensive risk management discipline, both building cybersecurity processes and integrating cybersecurity into business workflows drives many functional decisions.
1. Cybersecurity is becoming a primary factor when evaluating new technology.
Fifty-eight percent of companies view cybersecurity as a main consideration when assessing new initiatives. But firms are still treating cybersecurity as a secondary factor, or even an afterthought, opening the ecosystem to vulnerabilities and cyber risk and cybersecurity incidents.
2. Cybersecurity is impacting other business activities.
We see this happening in a few ways:
- Threat intelligence now includes new types of cyber threats like social engineering and ransomware attacks that highlight the intersection of technology and reality.
- The web of regulatory issues and government agencies overseeing digital business is driving organizations to become more cognizant of how they conduct business.
- As remote and hybrid work continues, the responsibility of the individual employee to maintain secure practices, via workforce education, has never been higher.
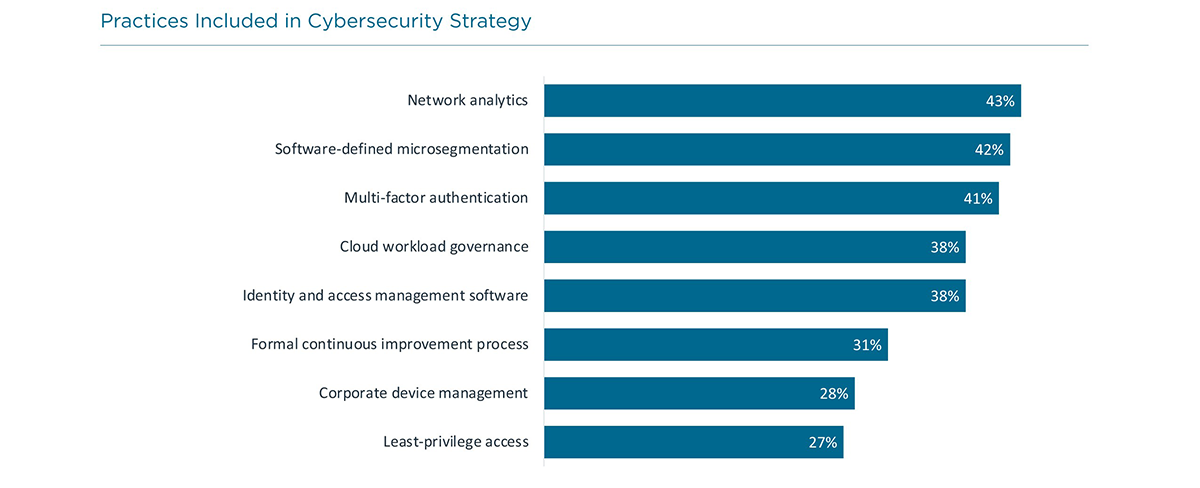
Although only 28% of firms identify a zero trust framework as part of their cybersecurity strategy, there are more firms following individual practices that are commonly included in a zero trust approach.
People: Talent Pipelines Get Stronger as Firms Build Skill Resilience
The cybersecurity workforce is growing. There were 660,000+ cybersecurity-related job openings in the United States between May 2022 and April 2023 – a 28% increase from the same time period in 2020 during the pandemic.
What’s Your Biggest Cybersecurity Challenge? See what our respondents said:

The top challenge in pursuing cybersecurity initiatives is now cybersecurity skill gaps. One strong option for bridging that gap is to bring in less experienced cybersecurity professionals who continue building their skills while becoming familiar with your corporate culture and objectives.
Regardless of the hiring pathway, there are bound to be some skill gaps that remain when new individuals are brought into an organization or when internal employees transition to cybersecurity from a previous role.
Developing a regular skill assessment regimen based on industry expertise and best practices is a key step in understanding the exact nature of the gaps that need to be filled.
What About Using Third Parties? See what our respondents are doing:
Today, organizations are taking a more comprehensive approach to selecting providers to protect their critical infrastructure. End users are looking for outside firms who understand modern cybersecurity threats, endpoint mitigation and have access to threat intelligence.
Product: AI Drives the Cybersecurity Product Set to New Heights
Generative artificial intelligence (AI) has been the buzz. Many believe this new wave of AI is the biggest tech paradigm shift in decades. But many companies have been using AI for some time:
- 56% of respondents indicate they already work with AI and machine learning (ML).
- 36% say they have not worked with AI or ML but are exploring the possibilities.
What Are the AI Possibilities for Cybersecurity? See what our respondents said:
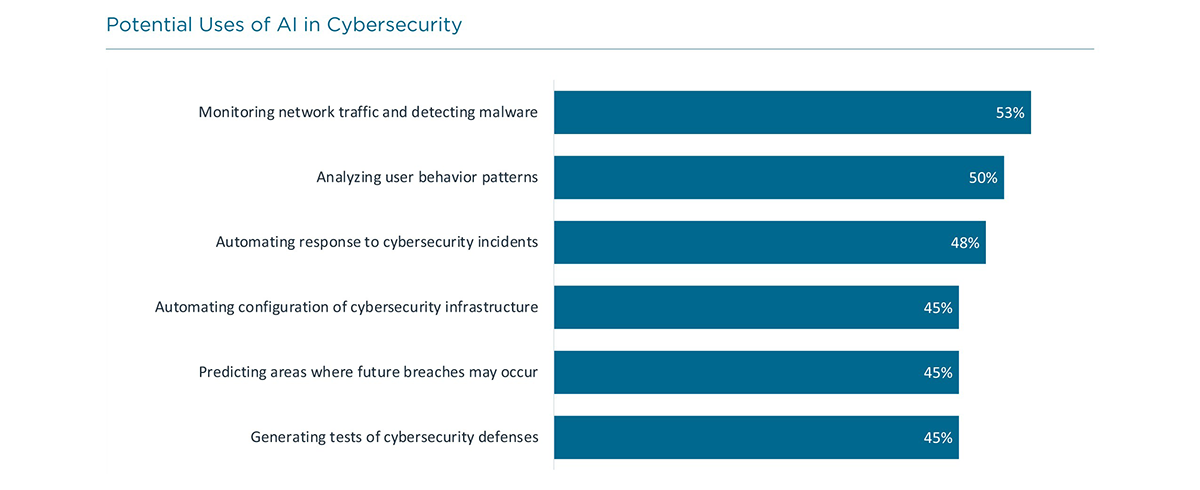
Of course, AI is like other emerging technologies. It’s not a standalone product by itself, but rather an embedded component of other products:
Our cybersecurity resources have been steadily expanding over the past few years, and now the challenge of managing a wide variety of cybersecurity tools is compounded by weaving AI capability into each one.
Methodology
This quantitative study consisted of an online survey fielded to business and IT professionals involved in cybersecurity during Q2 2023. A total of 511 professionals based in the United States participated in the survey, yielding an overall margin of sampling error at 95% confidence of +/- 4.4 percentage points. For international regions (ANZ, ASEAN, Benelux, DACH and UK/Ireland), a total of 125 professionals in each region participated in the survey, yielding an overall margin of sampling error at 95% confidence of +/- 8.9%. Sampling error is larger for subgroups of the data.
As with any survey, sampling error is only one source of possible error. While non-sampling error cannot be accurately calculated, precautionary steps were taken in all phases of the survey design, collection and processing of the data to minimize its influence.
CompTIA is responsible for all content and analysis. Any questions regarding the study should be directed to CompTIA Research and Market Intelligence staff at [email protected].
CompTIA is a member of the market research industry’s Insights Association and adheres to its internationally respected Code of Standards and Ethics.
About CompTIA
The Computing Technology Industry Association (CompTIA) is a leading voice and advocate for the $5 trillion global information technology ecosystem and the estimated 75 million industry and tech professionals who design, implement, manage and safeguard the technology that powers the world’s economy. Through education, training, certifications, advocacy, philanthropy and market research, CompTIA is the hub for advancing the tech industry and its workforce.
CompTIA is the world’s leading vendor-neutral IT certifying body with more than 3 million certifications awarded based on the passage of rigorous, performance-based exams. CompTIA sets the standard for preparing entry-level candidates through expert-level professionals to succeed at all stages of their career in technology. Through CompTIA’s philanthropic arm, CompTIA develops innovative on-ramps and career pathways to expand opportunities to populations that traditionally have been under-represented in the information technology workforce.
Read more about Cybersecurity.

 Download Full PDF
Download Full PDF