Section 1:
Market Overview
Key Points
- The multi-‐faceted mobility ecosystem presents many challenges to IT professionals, who must cede control in several areas to implement mobility solutions. The IT professionals and solution providers that can address these challenges will be able to tap into a growing market—research firm MarketsandMarkets estimates the BYOD and Enterprise Mobility market to grow at 15% CAGR, reaching $181 billion by 2017.
- While mobile devices are growing in market share of compute cycles, the overall computing market is also growing. Shipments of smartphones and tablets are expected to exceed shipments of desktops and laptops in 2013, but desktop/laptop shipments are holding steady rather than being replaced by the new devices. Enterprise behavior also suggests that mobile devices are being treated as add-‐ons, not replacements.
- The top drivers for mobility strategies are extremely mobile employees and mobile-‐optimized connections with customers. More advanced uses—such as enabling mobility consistently across an entire workforce or implementing mobile commerce—have the highest levels of future interest. Furthermore, companies are beginning to look towards more advanced uses of mobility, such as geolocation, omnichannel retailing, and machine-‐to-‐machine systems.
Taking Stock of Enterprise Mobility
In a relatively short period of time, mobility has become one of the hottest trends in technology. Much of this momentum is fueled by consumer interest, where smartphones and tablets have changed the mentality towards computing and created entirely new systems of value. As a proof point for how mobile computing is changing the technology landscape, Gartner predicts that 2013 will be the year that mobile phones surpass PCs as the most common web access device worldwide. Just as the Internet transformed the way in which businesses reached out to their customers, mobile devices are changing the way in which those customers want to connect with businesses. And, of course, the customers are only half of the equation; employees are also pushing to use this technology to give them more flexibility.
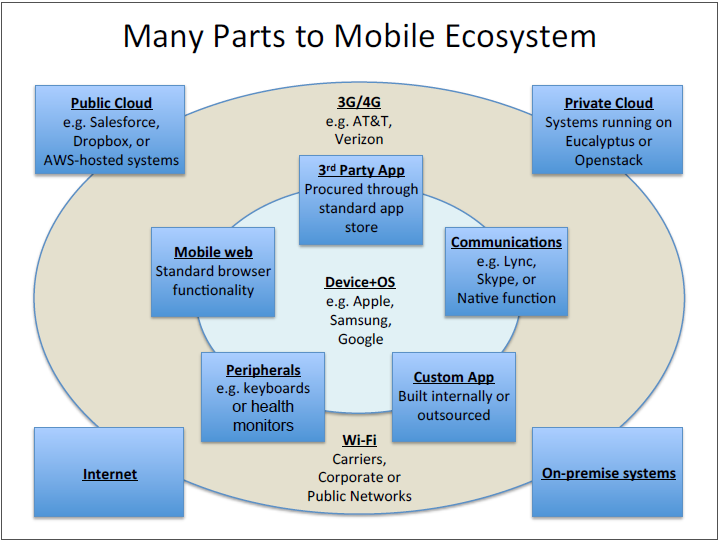
From an enterprise perspective, the mobile ecosystem—in conjunction with cloud offerings—presents a significant shift in control. Rather than having tight control over the entire experience, IT architects now must contend with devices that often serve dual purposes (personal and business use) and connect to third party systems. Between app developers, cloud providers, wireless carriers, and device OEMs, there are now many parties that can influence function and workflow. This leads to many questions in the mobility space, such as:
- Who is in charge of the physical device?
- Who controls the software on the device (including the OS)?
- Who controls the way the device connects?
- How secure are the backend systems that are accessed through mobile apps?
The answers to these questions cannot simply come from a central IT command center thanks to the nature of mobile offerings. Enterprise mobility is one of the primary focal points in the larger trend of the consumerization of IT. The most cutting-‐edge technology is now being created with the consumer in mind rather than being developed for business purposes, and that technology is coming into the enterprise through the back door. For most IT departments, shutting off this behavior is neither practical nor desirable—the benefits that come as a result of enabling workers on mobile devices are too great to disregard.
With a large number of subcategories under the broad mobility umbrella, it is difficult to size the overall market. Research firm MarketsandMarkets provides one general estimate, projecting the BYOD and Enterprise Mobility market to grow from $67 billion in 2011 to $181 billion by 2017 (estimated CAGR of 15%). MarketsandMarkets defines this segment as the services and tools used to provide secure and smooth connectivity solutions for an organization’s mobile workforce. This includes solutions such as Mobile Device Management (MDM), Mobile Application Management (MAM), and Telecom Expense Management (TEM). Any tools or services used for optimizing Internet offerings or connecting with customers in a mobile environment are not included.

Needless to say, there are sizable opportunities in the mobility spac as companies deal with providing access in a world where perspectives on computing are changing. CompTIA’s 2nd Annual Trends in Enterprise Mobility report studies the mobility behaviors of organizations across a wide range of industries and offers insights on the future direction of the enterprise mobility market. With 98% of companies in the survey claiming some amount of mobile solution adoption, this trend already shows extremely broad appeal and will have a high level of impact as it continues to evolve.
Add-On Or Replacement?
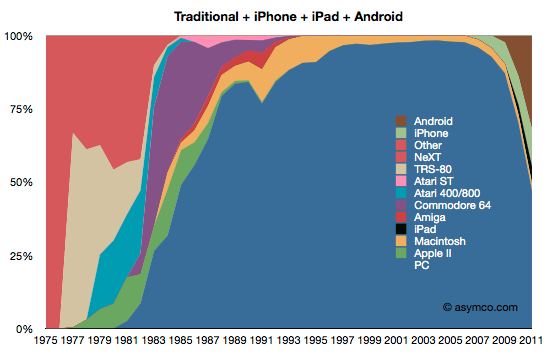
One of the most interesting questions in the mobility market is the extent to which mobile devices are supplementing established computing models vs. acting as replacements. A study of computing market share from analysis firm Asymco shows how the mobile operating systems iOS and Android are now accounting for greater market share than Microsoft Windows. This data has been widely reported and certainly indicates a shift of some type in the computing market. Not only must businesses consider how work gets done on mobile platforms, but there is also a need to provide some level of continuity as people are shifting between platforms.
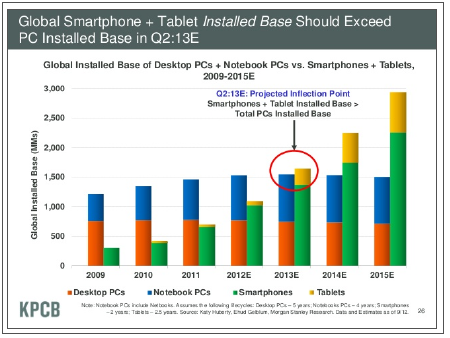
This need for continuity is more clearly demonstrated when assessing the overall base of computing devices currently in use. Smartphone and tablet growth is rising steeply; as with web access devices, the overall base of these mobile devices is expected to exceed that of desktops and laptops in 2013. However, while desktop and laptop growth has slowed dramatically and has likely reached a plateau, those systems still represent a large number of computers that are in use. Some types of compute cycles may be getting stolen by mobile devices, but it is not a one‐for-one replacement.
The tendency towards treating mobile devices as supplements to desktops/laptops can also be seen in corporate budgets. When considering how budgets for mobility are impacting budgets in other IT areas, there is some predictable movement—increased budget for Wi-Fi networking and cloud services, and decreased budgets for laptop support and perimeter security. However, this movement is relatively small, and approximately one third to one half of companies stated that mobility budgets had no impact on budgets in other areas. If mobile devices were acting as replacements, one would expect to see much more dramatic shifts away from desktop/laptop purchasing and into areas such as application development.
Viewing mobile devices as supplementary does not necessarily simplify the task of incorporating them into the corporate environment. Securing mobile devices and producing a consistent experience across multiple form factors are activities that need to take place regardless of how mobile devices are being used. As enterprise mobility matures, companies will move from these steps to more in-‐depth analysis of workflow and employee needs, optimizing device selection for the work that needs to be done.
Mobile Job Opportunities
With a topic as broad and complex as mobility, there will inevitably be a demand for new skills that can help businesses take advantage of the new prospects. Sometimes these skills are slight modifications to skills that already exist, and sometimes they are very new and must be built internally or found on the open market.
Mobile app development is the prime example of a hot job in the mobility space. As companies seek to build new offerings or to attach mobile front-‐ends to legacy applications, they are pursuing the necessary skills in mobile coding practices and languages (such as Objective-‐C, Ruby, and Node.js). A March 2013 snapshot of job trends from Indeed.com shows that while postings for mobile application developers have dropped from their highest point, they are still very high compared to three years ago.

A number of other job postings show a similar tendency. While similar to existing jobs, knowledge of the mobility market is a critical component in both technical and non-‐technical positions.
| Examples of Technical Positions | Examples of Non‐Technical Positions |
|---|---|
|
|
Mobile Usage Now and in the Future
Comparing this year’s results to CompTIA’s inaugural mobility report in 2012, most businesses are still focusing on the same areas as they build their mobility strategy. Providing support to the segment of the workforce that is the most mobile is still a top priority. Employees who permanently work from a home office currently receive the same amount of focus as last year, but future interest is heading in a positive direction.

Similarly, companies are continuing to look for ways to connect with their customers in a mobile environment. Examples could be offering customer support or pushing out special deals through mobile devices. With mobile phones becoming the most common web access device, the ability to make these types of connections in an optimized fashion is becoming very important.
Mobile commerce stands apart as a specialized form of customer connection. This could include revenue generated through apps, use of mobile devices as point-‐of-‐sale systems, or customized solutions for selling goods or services through mobile channels. Much more effort goes into building a mobile commerce practice, from securing financial information to providing consistency between mobile sites and other Internet or physical storefronts. As with last year, mobile commerce ranks as the lowest area of focus for businesses at this time, though it is also the area with the highest amount of future interest.
This shift towards more extensive mobile undertakings will occur internally as well. Since support for permanent telecommuters is a mid-‐level priority, it is reasonable to assume that most businesses are just beginning to explore novel ways to utilize mobile technology within traditional office situations. Section 2 of this report will study the viewpoints that companies have on the compute needs of their workforce and the devices used for work purposes; re-‐imagining workflows to take advantage of available technology can change these viewpoints and potentially lead to greater efficiency.
This re-‐imagining will be in a state of flux for several years to come, as mobile technology continues to expand with new offerings that provide value for businesses. The data shows that early adopters have started to experiment in several emerging areas, with large numbers of companies watching intently from the sidelines and planning their own future investments.
- Geolocation. Naturally, customers on the go have started using their mobile devices to find businesses of interest close to their current location. For businesses to flip this model and reach out to customers based on proximity raises some privacy concerns but also provides a rich contextual opportunity. Companies that successfully navigate the privacy issues through customers opting in or through some other model are able to proactively reach out with advertising or deals—a tactic that is likely to drive increased sales with tech-‐savvy customers.
- Omnichannel approach. This represents the ultimate goal of the aforementioned convergence between offerings in mobile commerce and pre-‐existing sales portals. Rather than view one channel as cannibalizing another channel, this approach seeks to combine all channels—mobile, Internet, and in-‐store—into a complete user experience.
- Machine-‐to-‐Machine (M2M). Familiarity with managing mobile devices and securing mobile data can be a foundational step towards success with M2M systems, where intelligent devices collect data and react to centralized analysis of that data. In addition to mobility skills, M2M systems may require skills in cloud computing and Big Data, making these systems most accessible by those companies who are on the leading edge of technology adoption.
Section 2:
Workforce Needs and Device Provisioning
Key Points
- In assessing the compute needs of the workforce, many companies do not project much change over the next two years. This could signal a lack of foresight in considering how different mobile devices with different capabilities can be matched to the actual work being done. To optimize use of mobility, companies should first consider modifying workflows to take advantage of available technology.
- Sixty-‐four percent of companies allow or mandate employees to bring their own devices. The primary motivator is increased productivity; only 12% say they follow this practice because it is too difficult to stop employees from using personal devices. The focus on managing BYOD is shifting to include BYOA—Bring Your Own Apps—as employees are also using those applications and services with which they are most familiar.
- As with compute needs, many companies do not foresee much change in the way they distribute bundles of devices. Over the next two years, 34% of companies expect to provide comprehensive bundles (such as laptop + smartphone + tablet) to employees. With only 13% of companies saying there is heavy integration of mobile devices with corporate systems, this is a prime opportunity area for IT departments and solution providers.
Assessing Workforce Needs
Information technology is in a period of high volatility, and one of the factors contributing to this is the phenomenon known as the consumerization of IT. This trend has many aspects, from the devices that end users are choosing to the user interface and experience that is becoming expected from software applications. The driver for all of this behavior is the fact that today’s top technology is being designed for consumers—a massive shift from the previous era of enterprise needs driving technology development.
The area of mobility is perhaps the field where this trend is having the most impact. For decades, employees have been pushing the issue of a more flexible work arrangement, and they now have the devices and network capabilities to turn this vision into reality. Laptops provided the first step towards a more mobile workforce, but IT departments were able to exercise a high degree of control over these computers and extend existing policies on security or data management. With smartphones and tablets, there is an even greater opportunity to extend productivity and flexibility but far less ability for IT to set up devices with a corporate image.
From observations of the mobile landscape, the general feeling among IT departments almost seems to be one of helplessness with respect to controlling the influx of devices. This helplessness, though, stems from the fact that the business perceives a high value in accommodating mobile devices. Balancing end user needs with IT requirements is the major challenge for businesses pursuing a mobility strategy, and most of the current activity in this space revolves around making decisions around devices—provisioning, securing, and allowing access to existing systems.
As strategies mature, companies on the leading edge of implementing mobility may take more of a proactive approach. Rather than focus on the devices, these companies may assess the specific needs of their workforce and match the device plan to those needs. There may still be provisions in place for employees who choose to supply their own devices, but corporate-‐liable devices will be driven more by business needs.
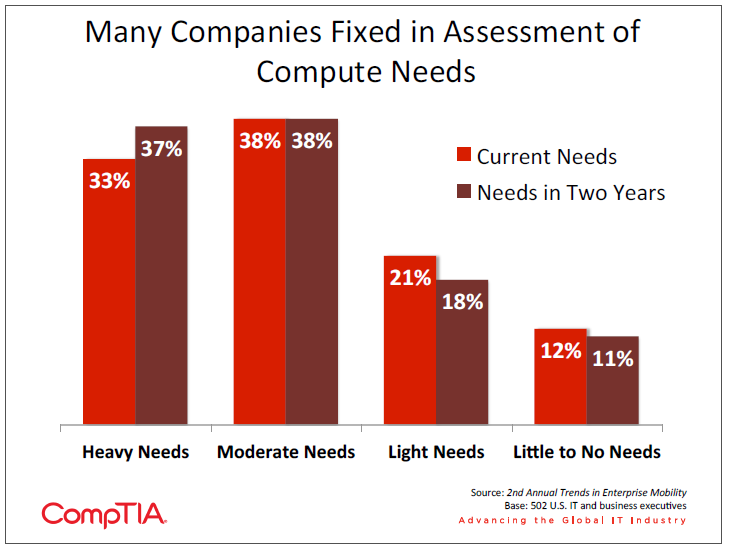
At this point, most companies are not taking that step. When asked to assess compute needs across their workforce, there was very little difference between the view of needs today and the view of needs two years into the future. There is a good probability that these viewpoints are influenced by a historical perspective on devices. Many workers may be using full service laptops, even if they simply need to check email or perform simple tasks within a small set of applications; similarly, many workers may not currently require any computing device, but access to information could increase efficiency or level of service.
For maximum benefit, workflow changes will need to be considered prior to evaluating workforce needs. Obviously, this is not a trivial matter, and companies would need to weigh the costs of operational disruption and change management against the potential advantages. Even though this may not be a path many firms are currently taking, it is worthwhile considering the opportunities that exist in consulting and implementation as this stage of enterprise mobility begins.
To BYOD or Not To BYOD
For now, the focus remains on devices, and the first step in building a proper device strategy is deciding who will provide the devices and which devices will be provided or allowed. From here, decisions can be made on security or application delivery, but it is difficult to build policies in those areas without a defined policy for devices.
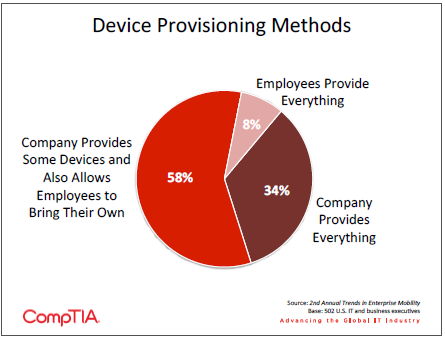
Although BYOD has received a great deal of attention, the majority of companies still provide at least a subset of devices to employees. A full third of companies strictly mandate which devices can be used for work purposes and do not allow any type of employee-‐provided device. The most popular option is to have a mix of corporate-‐liable and individual-‐liable devices. There is no “best” scenario—each company must make its own decision based on several factors, including security concerns and the amount of effort required to support the decision on devices.
For the companies that provide at least some devices to employees, the top two reasons were to standardize and consolidate IT support (39%) and that it is more cost effective to provide devices rather than a stipend (31%). This reasoning is contrary to the school of thought suggesting that BYOD can be a cost-‐savings move, suggesting one of two options: 1) BYOD actually is not more cost-‐effective or 2) many companies have not fully put forth the effort to compare costs or determine how to make BYOD more cost-‐effective. Best practices will emerge that might change the cost dynamics, but BYOD could be similar to cloud computing in that cost savings may not be a primary benefit and companies find other compelling reasons to pursue the strategy.
Another reason that companies provide devices is to ensure that security is adequately addressed. Twenty-‐three percent of companies say that ease of security is a reason for providing corporate-‐liable devices, and 7% say that compliance regulations dictate that work is done on controlled devices. Most likely, these respondents lie within the segment of companies who provide all devices to employees, since allowing user devices creates security issues that must be dealt with separately.
The security issue is broadening as companies realize that BYOD leads to BYOA—Bring Your Own Apps. Obviously the device itself is only part of the mobility equation, and apps and data access complete the picture. Along with being familiar with their personal devices, employees are building familiarity with a range of applications and cloud services. If they view these as more productive than tools provided by the company, they may move corporate data into their personal apps without fully considering security implications.
By a large margin, the top reason companies give for allowing employees to use or select their own devices is to increase productivity while employees are away from the office. Fifty-‐three percent of the population offered this as a motivation, with less than 1 in 5 giving other reasons, including allowing employees to use familiar devices or the aforementioned cost-‐cutting attempts. It is encouraging to note that just 12% highlight the fact that it is simply too difficult to stop employees from using their own devices. A business strategy should not be overly reactive to employee actions; otherwise, there may not be enough consideration toward business objectives.
As an early sign that some companies are tying device strategies to workforce needs, the companies who generally estimate light computing needs among their workforce show a much stronger tendency towards individual-‐liable devices. From this group, 16% do not provide any devices to employees, double the average across all companies.
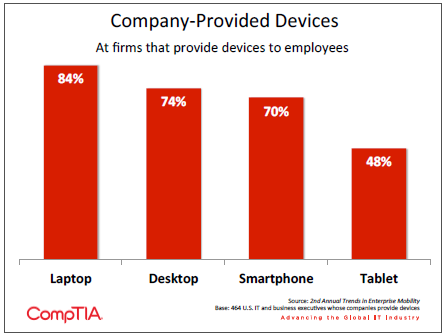
For the companies that do provide at least some devices to employees, the types of devices that they provide act as another data point suggesting that mobility is being treated more as an add-‐on than a replacement for current computing styles. Laptops and desktops still lead the pack, with smartphones close behind. The high percentages suggest that many employees are still operating with at least two devices, and Forrester corroborates this, reporting that 66% of employees use 2 or more devices at work. Tablet penetration is respectable as well, and the adoption rate is high enough to reasonably expect a lower percentage of laptops being provided if the tablets were acting as a replacement. This trend will be one to watch in future years.
Bundling strategies also follow the same pattern as compute needs. CompTIA’s survey defined four types of device bundles that companies may provide to employees:
- Comprehensive (such as laptop/desktop + smartphone + tablet)
- Moderate (such as only desktop/laptop or desktop/laptop + smartphone)
- Partial (such as tablet + smartphone)
- Light (such as only tablet or only smartphone)
Looking two years into the future, the trend seems to be towards providing more computing ability rather than narrowing in on the optimal arrangement for each job role. As with compute needs, there is a slight decrease in the number of workers who require no computing device, but there could be even more drastic movement in this area in the future, especially as new form factors are introduced.
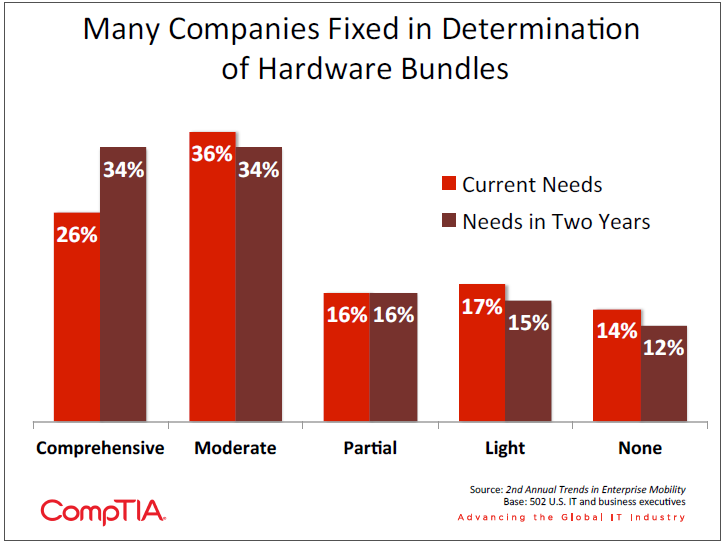
One of the challenges in providing a bundle of devices is integrating all devices into a consistent experience. Only 13% of companies say that there is heavy integration of mobile devices within their company, where custom mobile applications have been built to support business tools used in normal operations. The vast majority experience either minor integration (36%—mostly checking email) or moderate integration (45%—companies may be using cloud based software with associated mobile applications).
Just as BYOD has been addressed through Mobile Device Management (MDM), BYOA is being addressed through Mobile Application Management (MAM). In some cases, this may be a separate application; in other cases an MDM solution may be expanding to include MAM capability. Ultimately, the goal is to manage the entire suite of mobile solutions. As best practices in MDM and MAM emerge, they are forming the burgeoning discipline of Enterprise Mobility Management (EMM).
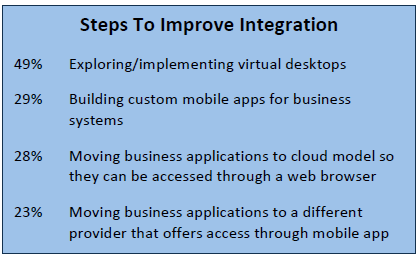
Even as companies are in an early stage of broadly providing mobile devices rather than optimizing workflows, integration is valuable work that will not be completely lost even if device strategies are modified. The different ways to improve integration involve a range of disciplines, so solution providers with various specialties can assist in the right scenarios. For example, virtual desktops are more strongly desired among companies with heavy compute needs, and cloud models are more desired among companies with light compute needs. Knowing the situation of each client and being able to project a future direction will help providers suggest and implement the best integration techniques.
Section 3:
Mobility Drivers and Strategies
Key Points
- The top two drivers for mobility adoption reflect the dual nature of mobility within the enterprise—62% of companies say they are driven by productivity gains and 59% say they are driven by employee flexibility. Optimizing Internet offerings for mobility ranks lower as a driver, suggesting that companies may be eyeing new opportunities before addressing current needs.
- Twenty-‐four percent of companies report having a formal mobility policy, up just 2% over the past year. However, the number of companies that plan to build a formal policy has doubled from 20% to 40% over that time. Additionally, companies see increases across the board with regard to the departments involved in building policy, indicating a holistic view towards mobile practices.
- Virtual desktops lead the list of technologies used to connect mobile workers to corporate systems and each other. This may be driven by early adopters who are testing the technology, but still indicates a potential avenue for dealing with a host of mobility issues. Other technologies used include VPN, videoconferencing, and VoIP.
Drivers and Benefits of Mobility
Although mobile solutions have been driven in large part by consumer desires and behavior, the trend would still not have as much momentum within the enterprise if there were not good business reasons for enabling mobile devices. In a way, mobility can be a win-‐win: employees get the flexible work arrangements that they want and companies gain some advantages that can help the bottom line.
This dual nature is reflected in the top two drivers for mobility adoption as rated by companies in the survey who have begun pursuing mobility solutions. Productivity gains are a fairly standard expectation with new technology, but with mobility it is an especially reasonable goal, given the familiarity that end users already have with mobile devices and applications. Employee flexibility works hand in hand with that goal by giving employees the ability to work from any location. In reality, “employee flexibility” may be a diplomatic way of stating things, since many companies at this time are likely reacting to employee-owned devices rather than proactively setting a strategy.
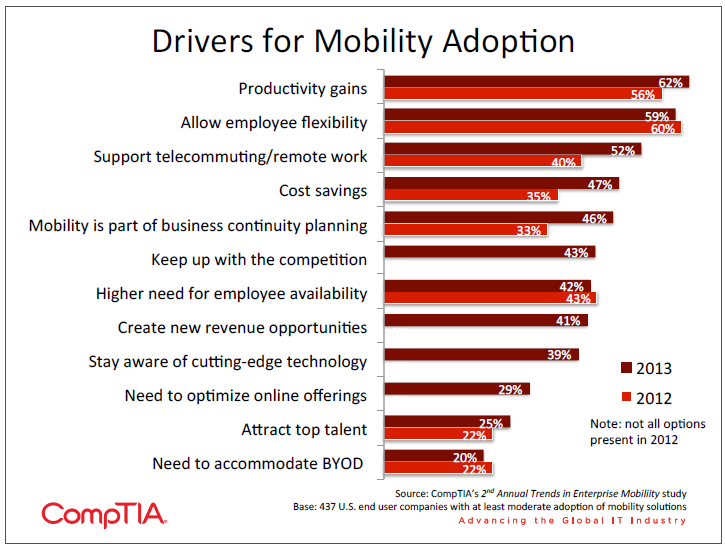
Cost savings is also listed as a driver for adoption, but as Section 2 described, mobility may follow the path of cloud computing in this area. An initial plan may show some potential for financial benefit, but hidden or unforeseen costs may ultimately erode the savings. Examples of possible unplanned costs are network upgrades, integration costs, or an inability to fully offload technology support from the IT department. This is not to say that mobile solutions provide no benefits—as with cloud computing, other benefits may still drive adoption even though cost savings do not materialize.
Indeed, the fact that cost savings, business continuity planning, and supporting remote work all saw significant increases year over year shows that companies are finding that there are many reasons to pursue mobility solutions. With such a broad range of mobility options available, businesses have the ability to explore several situations where mobility could play a role, then focus in on those scenarios which are most advantageous.
Drivers that are not related to creating a mobile-‐optimized workforce are lower on the list. Creating new revenue opportunities has the most appeal among small and medium businesses, where direct connections with customers and the need for mobile commerce are more likely. These firms may be intrigued by some of the more advanced uses of mobile technology, such as geo-‐location or omnichannel marketing. However, these firms also may not have the wherewithal to tackle these topics internally, opening the door for third party involvement.
It is interesting to note that the need to optimize mobile offerings ranks lower on the list than creating new revenue opportunities. This mirrors another trend taking place in technology: CompTIA’s Big Data Insights and Opportunities study highlighted the fact that many firms may be eyeing opportunities in Big Data, but they are not currently maximizing the use of their current data. Similarly, companies may be eager to find novel ways of using mobile applications for new revenue streams, but a first step would be to build out mobile-‐optimized versions of current offerings.
In practice, companies are finding that their objectives in building a mobility strategy are largely being met. Sixty-‐eight percent of the sample say that mobility has led to higher productivity, and 63% state that mobility allows employees to stay connected, providing the flexibility that they value. Fewer companies cite external benefits, which makes sense since fewer companies seem to be pursuing these avenues with a mobility strategy. Half of the sample reports that mobile solutions have led to improved customer engagement, and 34% say they have built opportunity for new market segments using mobile offerings.

Even in an environment where companies are reluctant to classify themselves as slow adopters of technology, mobility shows a remarkably high adoption rate. Only 2% of companies in the survey say they have no adoption of mobility. Mobility is certainly a broad topic, and companies who only deploy laptops could correctly classify themselves as adopters, even though that may not be the main focus of most mobility discussions. Another 11% rate themselves as having low adoption of mobility, and the barriers to greater adoption for groups on the lower end of the adoption scale are all manageable. Whether through demonstrating the importance of a mobile strategy in today’s business landscape or providing the technical know-‐how to integrate and secure solutions, IT firms that are well-‐versed in mobility will be well positioned to address the concerns of late adopters.
Building a Foundation for Mobility
In CompTIA’s inaugural Trends in Enterprise Mobility study, 22% of companies had a formal mobility policy in place. This was somewhat surprising, given the important role that formal policies can play in corporate strategy and security; but it was also viewed as a trend that was potentially on the rise, since an additional 20% of companies indicated plans for building a formal policy.
After one year, those plans have not borne much fruit. Only 24% of companies now report having a formal mobility policy. The largest amount of growth has been among small businesses, jumping from 7% to 16%. Here there is a similar situation as with creating revenue opportunities: these companies may have the least amount of bureaucracy to deal with in creating new policies, but they also may lack some of the skills necessary to build a robust policy that is enforceable and cognizant of all the technologies currently available.
There is still reason to believe that the trend towards building mobility policies will continue upward. The number of companies with a policy currently in place may not have grown much, but the number of companies planning to build a policy doubled to 40%. Even if the percentage of companies that follows through on these plans remains constant, there will be higher incidence of formal policies over the next year. It is also reasonable to assume that more companies will actually follow through as momentum around mobility grows and businesses take a more proactive approach.
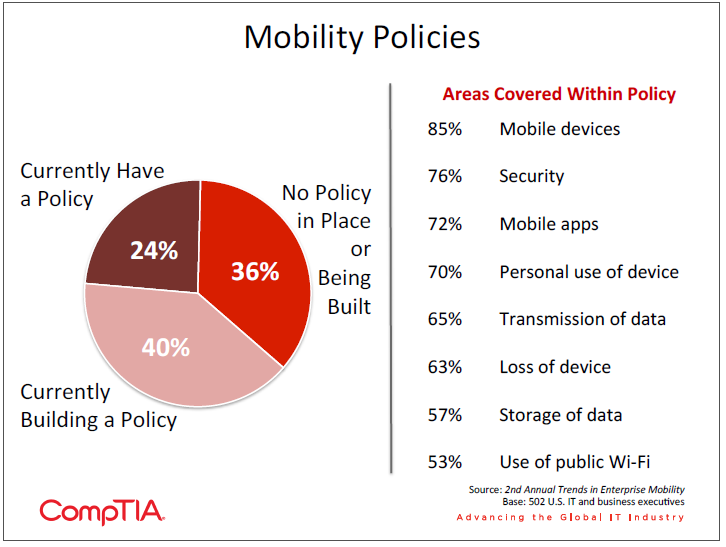
For those companies that already have mobility policies or are planning on building them, there are many areas that get attention. Devices, security, and apps naturally top the list. These areas of the policy may evolve over time as companies learn more about mobility and refine their plans. For example, an initial app policy may be that all downloads must be approved by the IT department. This could change if the organization decides to build an internal app store to store all approved apps, at which point a new process may arise for submitting apps for consideration.
Moving beyond these three primary topics, many organizations are beginning to consider some of the other facets of mobility. Although security is a top consideration, this may generally refer to device security, such as mandating passcodes or prohibiting jailbreaking. The use and storage of corporate data also falls within a security discussion, but it merits separate focus since the data is not an inherent part of the device. As data rapidly spreads outside an organization’s firewall, IT departments will need to do their part to monitor and protect data with the use of Data Loss Prevention (DLP) and other technologies. Users, then, will need guidelines within policies to govern usage (or at a minimum highlight awareness).
An interesting—and encouraging—note on mobility policies comes from the data related to the groups within a company responsible for building the policy. Across the board, involvement has increased compared to last year. This indicates that companies are taking a holistic approach to mobility, a tactic that has become necessary now that technology is deeply ingrained into all aspects of a business. While IT staff (74%) and IT executives (69%) are the primary parties involved, companies also see good engagement from business executives (48%), business staff (43%), and CEOs/owners (39%).
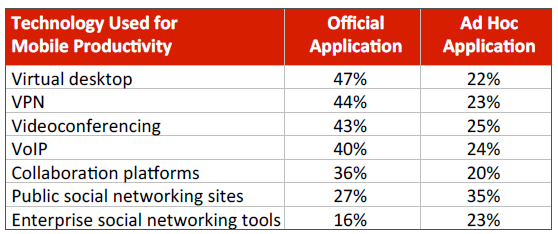
With policies in place, the second basic step in building a mobility strategy is to provide the tools that allow mobile workers to connect with corporate systems and with each other. As with policy involvement, nearly all technologies in the survey saw increased usage year over year, both as official applications supplied by the company and as ad hoc applications downloaded and used by employees on their own.
Virtual desktops saw the largest increase and led the list of technologies used. This does not exactly line up with anecdotal evidence, where virtual desktops do not seem to be adopted as highly as other technologies in the list. However, even among stories of lower adoption there is an acknowledgement that virtual desktops hold much promise for enabling work in a multi-‐device environment. The high adoption suggested in CompTIA’s survey may be a result of early testing among select users—usage rates are significantly higher for those companies that identify themselves as early adopters of mobility solutions. Additionally, respondents may have a loose definition of virtual desktops and consider browser-‐based applications within this category rather than taking the more strict view of full desktops running on virtual servers and provided to end users as an application on their device.
Videoconferencing also had a significant increase. Another technology that has long held substantial promise to improve communications, videoconferencing exists in many incarnations, from free consumer tools to expensive telepresence installations. All of these styles have experienced various hurdles, such as insufficient adoption to justify an investment or ease of use. However, technology improvements have gradually eroded these barriers, and the upcoming WebRTC protocol may contribute to a boost in adoption.
At the bottom of the list, there are technologies designed specifically to facilitate information sharing among large groups. Collaboration platforms and social networking tools are not currently as popular as other options, but they are also among the youngest technologies being put to use within the enterprise. As companies build best practices in securely integrating these technologies, they will likely become valid options for connecting employees.
Integrating technologies in a complex landscape has long been a sweet spot for IT channel firms, and the needs presented by mobility are no different. Companies constantly cite a need to improve communications, and mobility offerings add a significant component to the puzzle of mixing technologies for efficient collaboration. By focusing on the technologies already at use within a company and integrating these technologies with new mobile solutions, IT firms can add substantial value to their clients’ mobility strategies.
Section 4:
Challenges in Building Mobility Solutions
Key Points
- The top challenge in implementing mobility solutions is the mobility skill of general staff, reported by 40% of companies. Even though employees may be using personal systems, they may not be aware of all the functionality, especially when it comes to security functions. The second largest challenge is making systems accessible securely, reported by 39% of companies.
- Sixty-two percent of companies cite the overall security of mobile devices as the greatest risk to supporting enterprise mobility. A lost device is the most common type of mobile security incident, but mobile malware is slowly becoming a threat to consider, especially in the Android ecosystem.
- As companies decide on their support structures for mobile workers, they should consider the extent of in-‐house support as well as the tools used for technology support. The most effective tool for mobile support is remote access, but this is also the tool with the lowest level of adoption.
Challenges in Implementing Mobility
With any technology, there will be difficulties in getting to the point where the promised benefits are actually realized. Integration, security, and end user adoption are all examples of common challenges faced when new technology is introduced.
With mobility, the challenges take on a unique quality. The devices that need to be integrated and secured have not necessarily been chosen by the IT department, so there is often a discovery phase where IT staff or solution providers must become familiar with the pieces they are dealing with, then determine the best way to move forward.
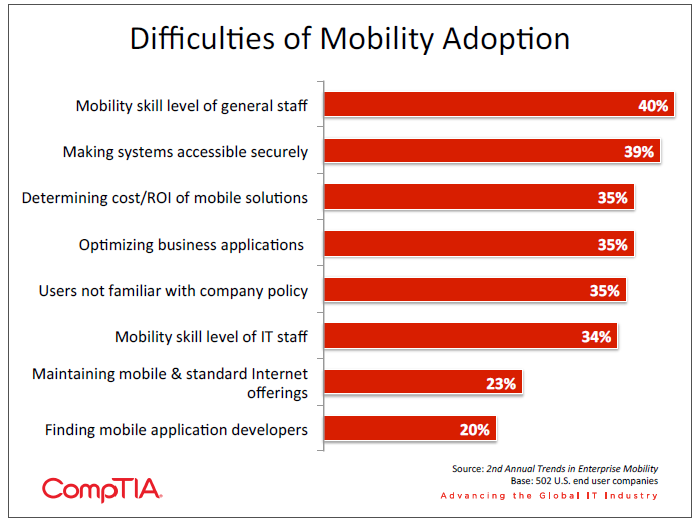
However, even though end users are causing problems by bringing in their own devices, it seems that they are also exacerbating the problems by not having a complete grasp on the devices’ capabilities. It stands to reason that most end users are familiar with a subset of capabilities, and features related to security or data encryption may be not be a standard part of this subset. When IT departments want these features turned on, then, there is both an unplanned learning curve and the potential for disrupting productive operation. More advanced techniques for addressing BYOD, such as Samsung’s KNOX technology or General Dynamics’ GD Protected suite of offerings, will also likely face an uphill climb in end user familiarity.
The second greatest challenge—making corporate systems accessible securely to mobile devices—points to an effort by IT teams to move away from the notion of a secure perimeter and instead provide a secure backend experience than can be accessed through any device or web browser. CompTIA’s 10th Annual Trends in Information Security study notes that mobility, along with cloud computing and social networking, has caused many security experts to acknowledge that a new approach is needed. The challenge then becomes procuring the necessary budget; for executives accustomed to paying out funds to bolster anti-‐virus or firewall, an architectural overhaul may be hard to swallow.
This overhaul plays into many of the other challenges cited. Optimizing business applications for mobile usage and maintaining consistency across all forms of Internet offerings is not a small undertaking, nor is it easily handled by a team skilled in maintaining legacy applications. Investing in the proper skills, whether through hiring or re-‐training of current staff, is a crucial step in building a robust mobile strategy.
A review of the skills required for mobility reinforces that there is work to be done. Companies rated their staff most skilled in the area of Wi-‐Fi networking, which makes sense since Wi-‐Fi is being widely adopted outside of efforts for mobility. Beyond that, less than one third of companies felt their staff had a high level of skill in many key areas, including mobile device management (29%), mobile security (27%), and mobile application development (21%). While workers in IT tended to have a more positive view of skill levels, they are still not overly bullish, indicating that gaps definitely exist.

Mobile Security
Most organizations view security as their top IT priority. This does not necessarily mean that the majority of IT budget or project time is spent on security—a company may believe that steps taken in the past to create a secure environment are still effective today. Mobility challenges that assumption in a fundamental way. The IT team is losing some amount of control over device selection and application usage, but they are still viewed as the primary party responsible for keeping assets secure.
By a large margin, security is viewed as the greatest risk to supporting enterprise mobility, with 62% of companies indicating that the overall security of mobile devices is a major risk. Nearly half the sample indicated the loss of a mobile device as a risk, a sub-‐topic that certainly falls within the domain of security. Compliance issues came next as a risk, with 38% of companies citing this as an issue.
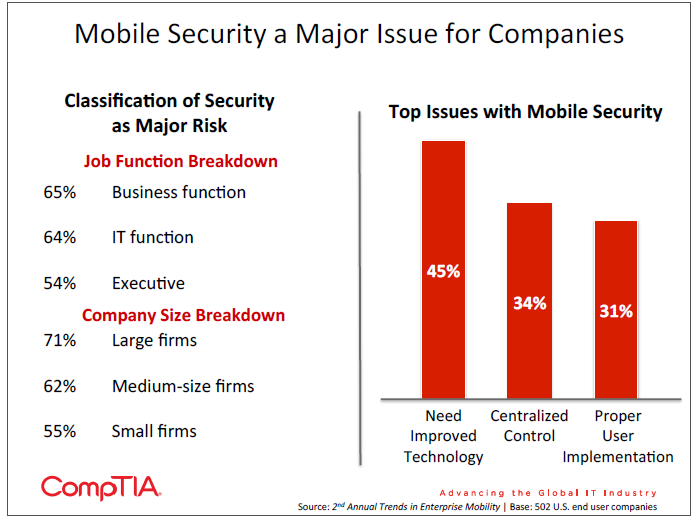
It is a positive sign that respondents in a business function rate security as such a high risk. Although they may still expect the IT function to manage security, this is a signal that they may be willing to tolerate certain security measures on their devices, as long as they are not too intrusive. The viewpoint of mobile security broken down by company size is not surprising—large companies tend to have more assets that they are concerned about protecting. However, recent analysis of attack patterns shows that cyber criminals also target the smallest companies at a high frequency since those companies typically have the lowest defenses. Criminals are finding ways to monetize nearly any type of information, and as a result all companies must take their digital security seriously.
As in CompTIA’s first mobility study, the need for improved technology is the top difficulty in implementing mobile security. With the percentage of companies viewing this as an issue rising over the past year (from 33% in the previous study), the available technology is clearly not meeting the market’s needs as more companies seek to safeguard their mobile investment. Tying back to the skill level of general staff with mobile solutions, the technologies available may be too intrusive or complex to operate seamlessly. Security professionals need options that will give them central control and management of devices without interfering with productivity.
The focus on mobile security is actually something of a rarity in the security domain: a proactive concern without some sort of major breach prompting action. To this point, there has not been a major corporate security incident involving mobile devices. The survey reflects this—the most common mobile security incident is a lost device (49%), followed by violations of company policies (28%). Only 24 of companies have experienced mobile malware, and 31% of companies say that have not experienced any type of mobile security incident.

There are two primary actions that have been taken as a result of any security incidents involving mobile devices. First, companies have begun requiring passcodes. Although this creates an inconvenience for users, the precedent of logging into a device for work purposes is well established and is a simple way of providing a layer of security. The second action commonly taken is to establish a procedure for lost devices. This is short of a full mobility policy but certainly addresses the most widespread type of incident. Other actions taken include requiring encryption on mobile devices, installing software for tracking/wiping devices, and holding additional training classes on mobile policies.
Mobility Support
IT support is one of the topics at the center of conversations around mobility within the enterprise. Many companies that are considering adopting a BYOD strategy include support in the decision process—the thinking is that users get the freedom to select their own devices and also take on the responsibility for maintenance and support, freeing up bandwidth for an IT team. Time will tell how valid this thinking is. In practice, some organizations may find this to work well and others may find it difficult or unproductive to force users away from in-‐house IT support.
As described throughout this section, the act of balancing end user needs and IT requirements is a major undertaking. This is another reason that transferring support responsibilities to end users may be ill-‐ advised: support to an end user means making the device as functional and productive as possible, not necessarily keeping it in line with corporate security objectives.
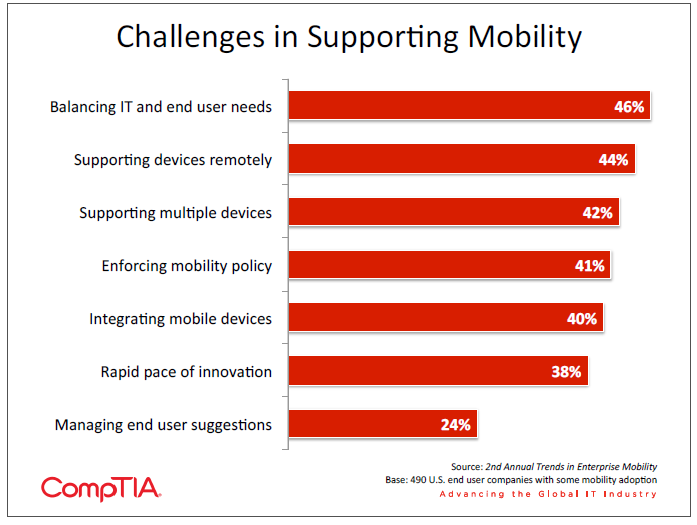
Remote support of devices is another issue that has existed for some time but is magnified in the current environment. Laptops have certainly required some remote support, but this task is made simpler when the equipment is limited to a small pool of options and corporate images can be installed. With a wide variety of mobile devices and limited ability to control the OS and applications, it is much more difficult to troubleshoot a problem remotely and provide a fix.
Following the trend from last year’s study, the use of remote access is viewed as the most effective tool for providing remote support but is also near the bottom in terms of adoption. Most companies are still relying on traditional support structures such as telephone, email, or online help desks. With solutions on the market now allowing remote access of smartphones and tablets, this is another area that companies should consider investing in as they seek to optimize productivity through the use of mobile devices.
About this Research
CompTIA’s 2nd Annual Trends in Enterprise Mobility study was conducted to build on previous CompTIA research in the mobility space and further explore mobility trends, challenges and opportunities. The objectives of this research are:
- Understand the variables and tradeoffs involved in a company’s decision on provisioning devices
- Ascertain benefits realized from using mobile/remote work solutions
- Identify the challenges in supporting and managing mobile/remote work
- Gauge the need for training and/or standards
Section 1: Market Overview
Section 2: Workforce Needs and Device Provisioning
Section 3: Mobility Drivers and Strategies
Section 4: Challenges in Building Mobility Solutions
The research consists of a quantitative online survey of 502 IT and business executives directly involved in setting or executing mobility policies and processes within their organizations (aka end users). Data collection occurred during February 2013. The margin of sampling error at the 95% confidence level for the results is +/-‐ 4.5 percentage points. Sampling error is larger for subgroups of the data.
As with any survey, sampling error is only one source of possible error. While non-‐sampling error cannot be accurately calculated, precautionary steps were taken in all phases of the survey design, collection and processing of the data to minimize its influence.
CompTIA is responsible for all content contained in this series. Any questions regarding the study should be directed to CompTIA Market Research staff at [email protected].
CompTIA is a member of the Marketing Research Association (MRA) and adheres to the MRA’s Code of Market Research Ethics and Standards.
Read more about Industry Trends.

 Download Full PDF
Download Full PDF