If you are like most executives, buying technology can be exciting, hopeful, uncertain, frustrating and everything in between. You must identify requirements, weigh competing needs, evaluate capabilities, assess ROI and consider a host of other factors – all of which can be overwhelming, especially when they involve mission-critical functionality like IT security.

The CompTIA Buying Guide for IT Security is designed to provide you with a starting point.
IT security has been a top priority for companies for as long as computing has been a business tool, but the methods for securing digital assets have changed as the use of technology has evolved to drive businesses’ value not simply support their operations. Cloud and mobile solutions have extended organizations’ boundaries well past what were once secure perimeters. And the data these tools generate is now fueling businesses’ decision-making and competitive advantage.
As a result, systems and data have never been more valuable or at risk of attack. What’s more, the threats are changing daily, making the evaluation and purchase of IT security solutions a complicated and challenging endeavor.
The Computing Technology Industry Association (CompTIA) designed this guide to assist you in navigating the decision-making process for an IT security engagement. This guide is not intended to be a Consumer Reports-style product review, but rather a framework for “asking the right questions” to ensure that you are making an informed decision.
In the last few years, we’ve seen dramatic shifts in enterprise technology. Organizations large and small have moved past early experiments with cloud computing to adopt a cloud-first strategy for implementing infrastructure and applications. Mobile devices have become ubiquitous, extending the computing platform and increasing productivity and efficiency. Digital data has grown in relevance as organizations collect data from new sources and extract new insights that fuel their decisions.
These new technologies -- cloud, mobile and big data as well as others -- are enabling digital organizations like yours, which rely on technology not simply to support operations but to drive business outcomes. These outcomes may include improved productivity, increased revenue, service innovation and competitive advantage.
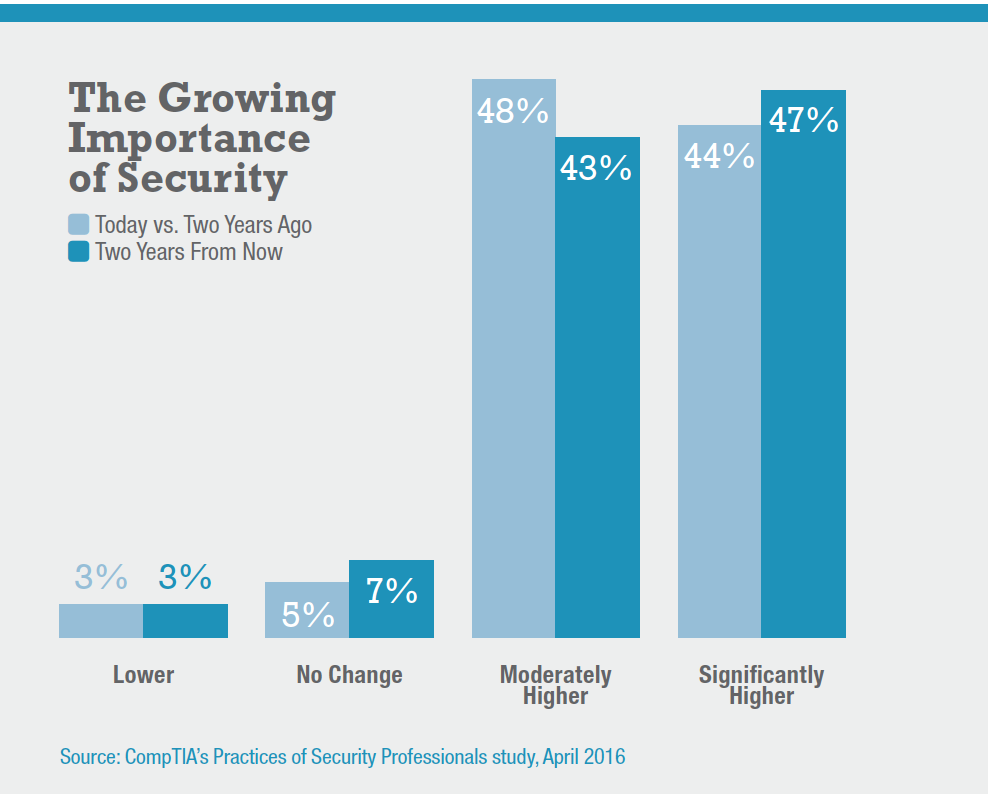
As technology grows in importance, so does the issue of security. Ninety-two percent of IT security professionals said the importance of security was higher today than it was two years ago, with 44 percent saying it was significantly higher, according to CompTIA’s April 2016 surey, Practices of Security Professionals. What’s more, similar numbers of IT security pros expect security to increase in importance over the next two years.
WHAT ARE THREATS TO IT SECURITY?
Security pros have good reason to be concerned because the potential for security breaches is very real. Seventy-three percent of organizations have been plagued by at least one security breach or incident in the past year, with about 60 percent of breaches categorized as serious, according to CompTIA’s International Trends in Cybersecurity report published in May 2016. The percentage of mobile-related security incidents – such as lost devices, mobile malware and phishing attacks or staff disabling security features – was even higher at 76 percent across 12 countries polled.
As more data and devices proliferate in cyberspace, the threats are expected to increase in number and cost. Intel Security ’s McAfee Labs 2017 Threats Predictions Report identifes several emerging and growing concerns , including the recently identified risks from IoT-initiated malware.

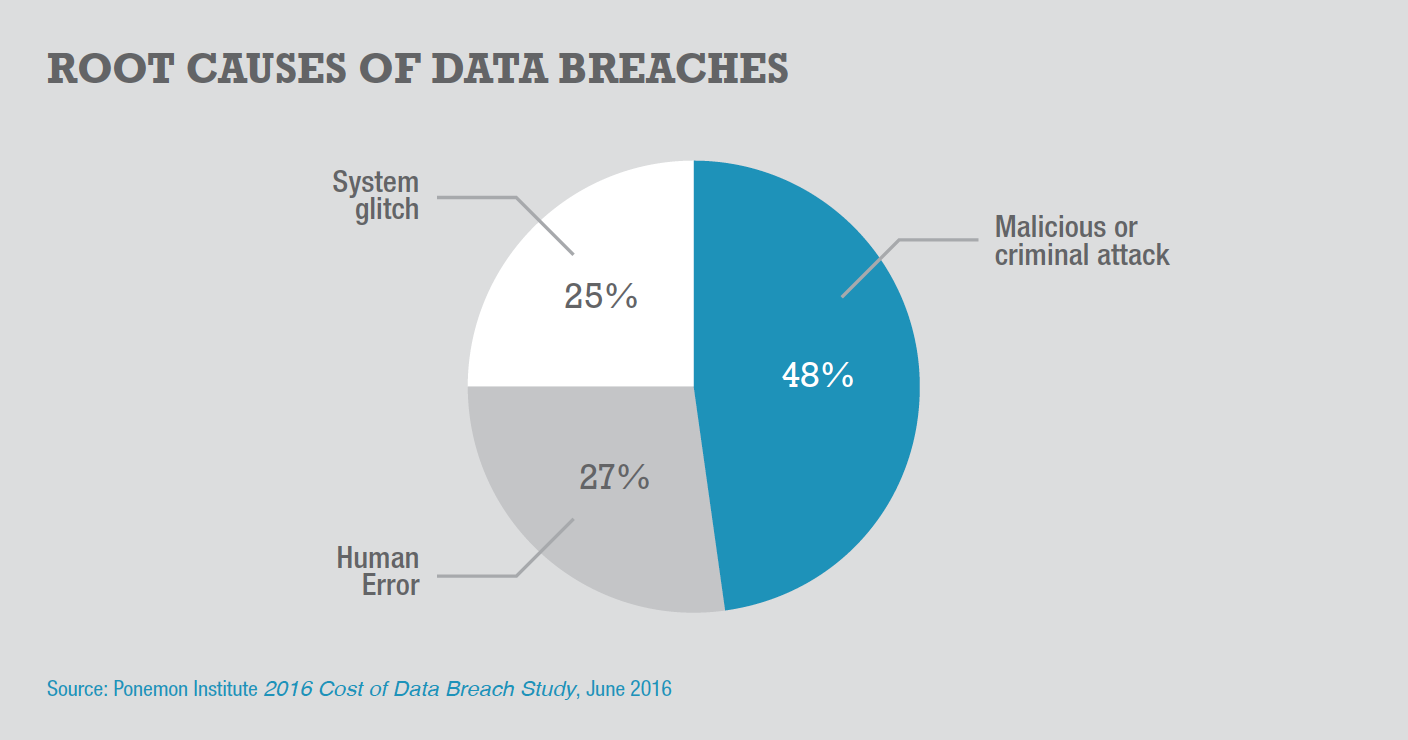
While nearly half of all security incidents are criminal attacks, Ponemon Institute’s Cost of Data Breach 2016 report says you also need to be aware of and prepare for those caused by negligent employees or contractors as well as those that involve glitches in IT systems or failures in business processes.
WHAT IS THE COST OF IT SECURITY BREACHES?
The costs associated with security breaches are going up, jumping 29 percent since 2013 to more than $4 million per incident in 2016, according to Ponemon’s annual benchmarking report. In addition, when it comes to the impacts of breaches – such as cost per record lost – Ponemon says the gap is widening between organizations that are unprepared and those that have added policies and processes like incident response plans, encryption and employee training.
To calculate the average cost of a data breach, Ponemon collects both the direct and indirect expenses as well as opportunity costs incurred by the organization as follows:
DIRECT COST – the direct expense outlay to accomplish a given activity, such as engaging forensic experts, outsourcing hotline support and providing free credit monitoring subscriptions and discounts for future products and services.
INDIRECT COST – the amount of time, effort and other organizational resources spent in the aftermath of a breach, such as in-house investigations and communications. This category also includes the extrapolated value of customer loss resulting from turnover.
OPPORTUNITY COST – the cost of lost business opportunities resulting from negative reputation effects after the breach has been reported to victims and publicly revealed to the media.
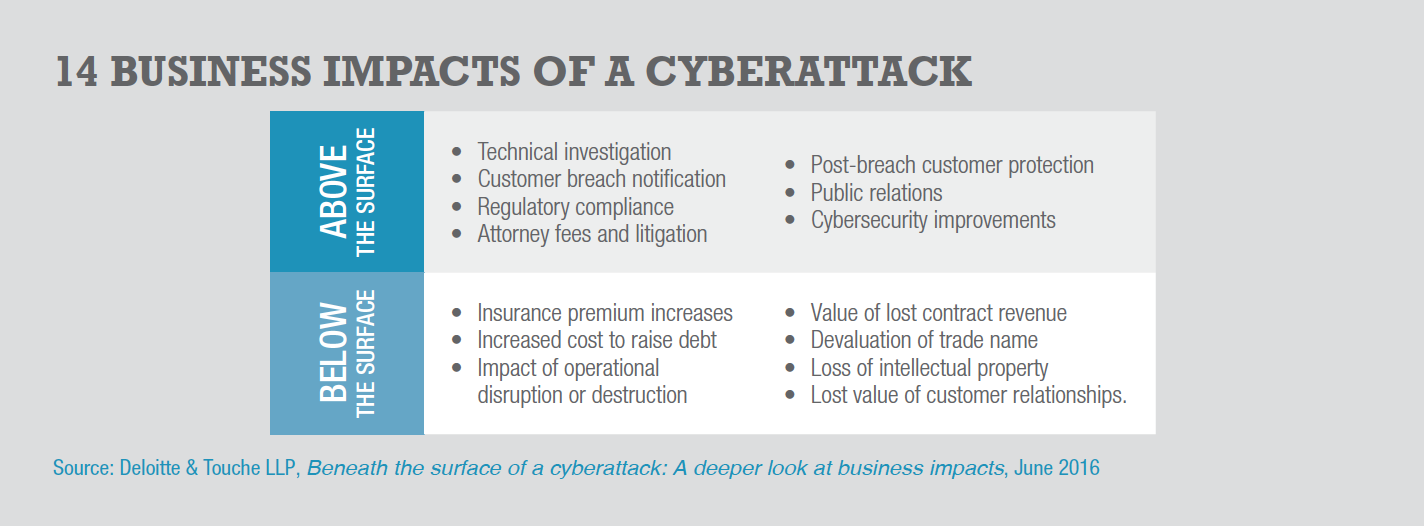
A 2016 report from Deloitte Advisory says the costs of a cybersecurity breach could be higher than most data show as the costs can rack up for many years after the initial incident. The from identified 14 cyberattack impact factors, including seven it claims are hiding beneath the surface and account for 95 percent of the financial impact. (see chart, “14 Business Impacts of a Cyberattack”).
HOW IS THE APPROACH TO IT SECURITY CHANGING?
As businesses push forward using new technology in innovative ways, they will need to consider a new approach to cybersecurity. The days of having a secure perimeter as the primary means of defense are fading for companies that want to use cloud computing or mobile solutions to enable their workforces to do business anytime, anywhere from any device.
Instead, there is are a series of shifts in thinking about IT security:
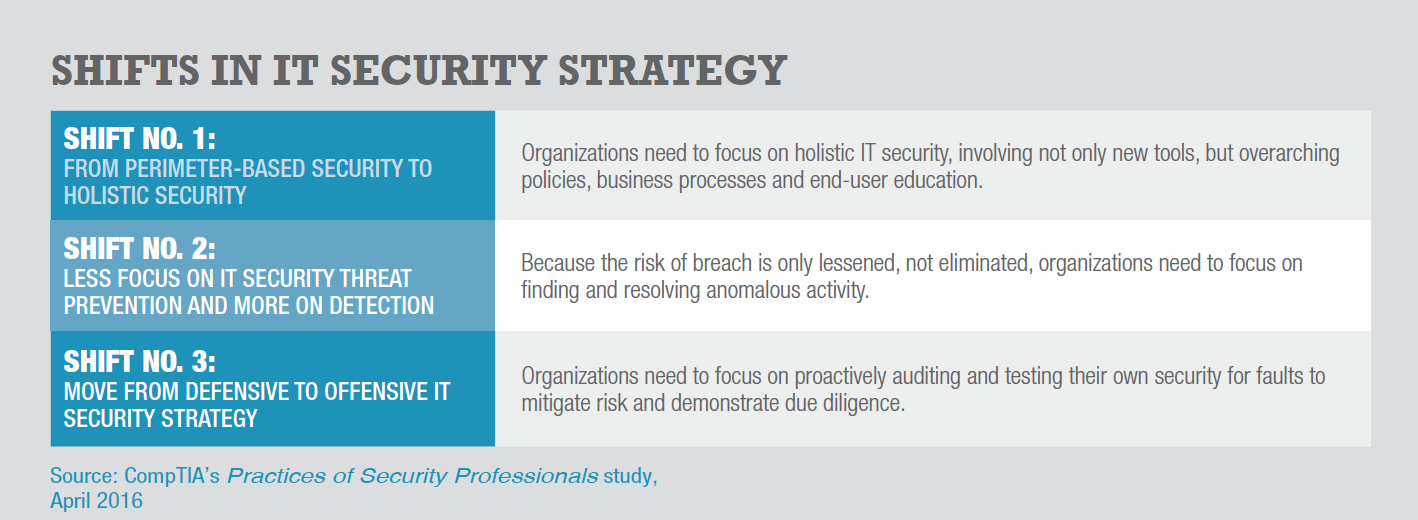
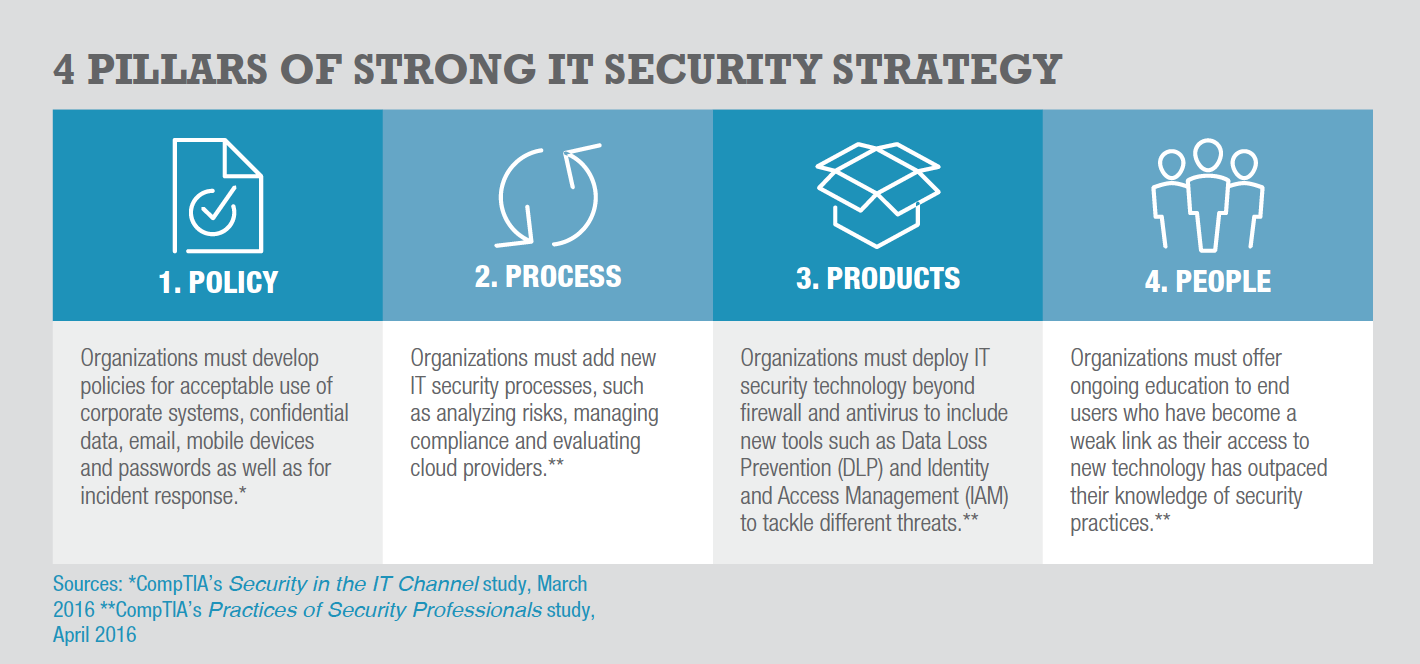
In addition, the overall focus on security has changed from departmental to organizational. Accordingly, the modern approach to IT security considers new technologies along with new processes and policies as well as human factors – collectively, the four pillars of a strong security strategy.
Any business investment decision requires that you weigh a range of factors, including the needs of your company’s stakeholders and alignment with your corporate objectives as well as the functional requirements, pros/cons and total cost of ownership (TCO) for each solution.
As a foundation for evaluating your potential investment in IT security, this buying guide reviews some of the considerations that should be factors in your decision. These include reasons to consider updating your security as well as likely challenges. It also will cover the primary things you need to evaluate, including your company’s risk tolerance, available security tools, human factors and your current security risk profile.
WHAT ARE THE DRIVERS AND CHALLENGES TO A NEW APPROACH TO SECURITY?
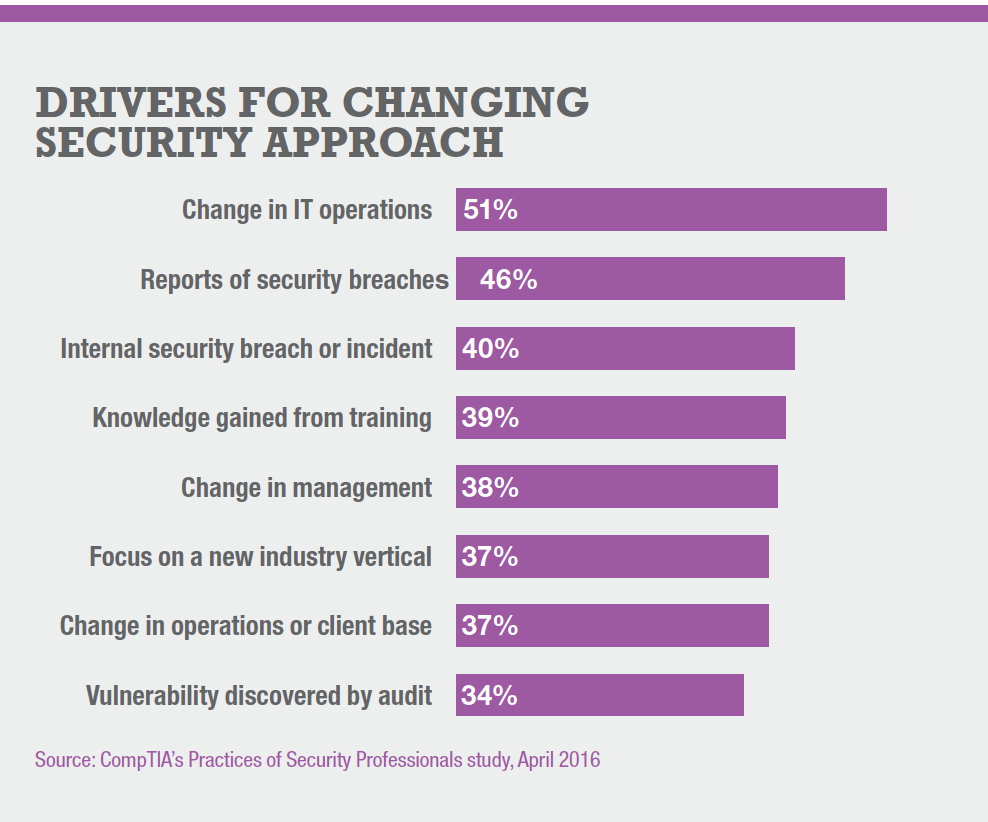
Simply acknowledging security as a high priority is unlikely to change behavior in your organization. There needs to be a starting point. If your company is like the majority, the driver is a change in IT operations, such as the shift to cloud and mobile solutions. Reports of security breaches – increasingly frequent in today’s headlines – or internal security incidents also are great catalysts for an IT security upgrade.
Despite overwhelming evidence that a serious focus on security is paramount, you may have trouble moving forward. The No. 1 reason for inaction is a (usually mistaken) belief that current security is “good enough.” This and most of the other obstacles are related to a lack of understanding about the need for security and the corresponding budget to invest. One way to tackle this is to enlist the help of a third-party IT adviser that can help arm you with the benchmarking data to make the business case.
Once your organization is onboard with an IT security upgrade, you need to consider four primary elements:
WHAT IS YOUR COMPANY’S IT SECURITY RISK TOLERANCE?
When the bulk of your company’s technology was on-premises, any data classifed as confdential could be placed behind a frewall. Today, maintaining very strong defenses for all your data and systems is simply too costly. So, a risk analysis is in order.
A risk analysis includes:
The time and effort involved in mitigation is directly related to the probability and impact. In other words, a “high probability/high impact” risk requires a more robust mitigation than a “low probability/low impact” risk.
This exercise can highlight those areas where a company may be either taking on too much risk or constraining their efforts because of overly stringent views on security.
WHAT NEW TOOLS ARE AVAILABLE TO IMPROVE YOUR COMPANY’S IT SECURITY?
Other items to consider when updating your IT security are the new tools that are available. Firewalls may not be a complete technology solution anymore, but they are still a critical piece of the toolkit. Companies may need to update their frewall, though, as the function has evolved from fltering traffc based on packet inspection to restricting traffc based on understanding of application behavior. Beyond the frewall, there are many new tools and techniques that a business might employ as they expand their IT footprint, such as Data Loss Prevention (DLP), Identity and Access Management (IAM). Security Information and Event and Enterprise Security Intelligence (ESI).

HOW DO YOU ADDRESS THE HUMAN ELEMENT IN IT SECURITY?
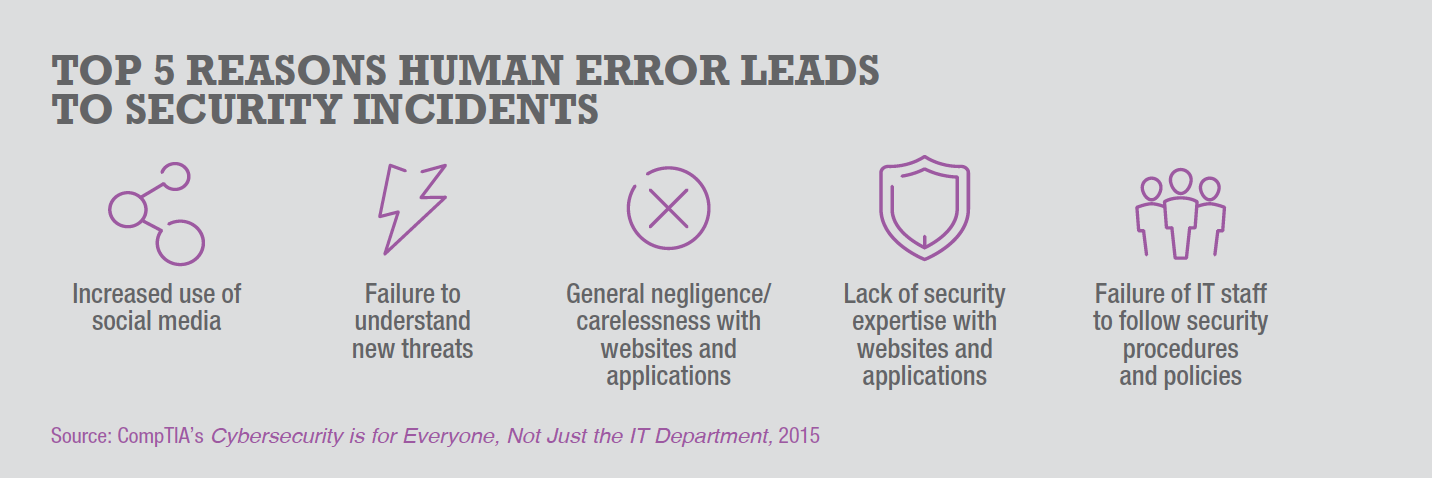
Another key variable in today’s security equation is the human element. CompTIA research shows that employees who are not following policy or simply do not have the expertise to notice security issues with technology they are using are the main cause of security breaches. This isn’t malicious behavior on the part of these employees, but simply an indication that they lack awareness.
The obvious solution to this problem is educating your employees, but delivering such training is a practice your company may need help with. The complexity of the security landscape means that security awareness cannot be gained through quick online refresher courses. Instead, end-user education should be:
Businesses on the leading edge of security training are using tactics such as simulating phishing emails to gauge the level of awareness, instructing the workforce on signs of a security incident, and eventually driving the desired behavior. Technology may provide some assistance with mitigating the human element, but ultimately training and policy will need to be updated to reduce the security risk.
WHAT IS YOUR COMPANY’S CURRENT IT SECURITY RISK PROFILE?
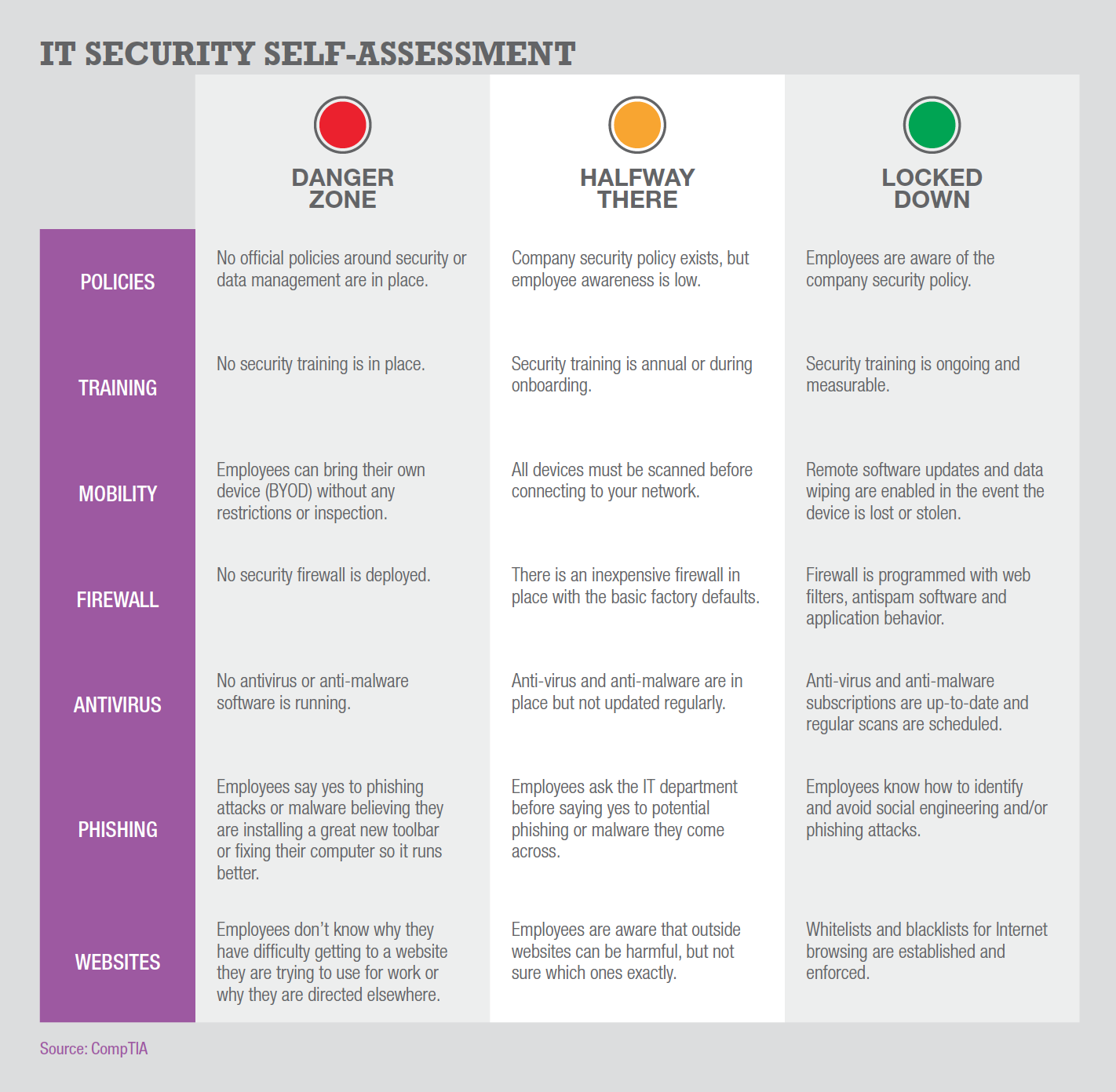
So what exactly is your organization’s security risk? One of the best ways to assess this is to engage a third-party security consultant. Professional auditors have both detailed security knowledge as well as real-world experience to help discover which security holes exist in your IT environment and which ones should be patched based on your company’s risk tolerance.
If an external audit is not an investment your organization is able to make, the alternative is a self-assessment. Without diving into technical details, the grid below describes certain behaviors you can self-identify to get a sense of where your company stands on the path to best practices.
As discussed earlier in this Buying Guide, IT security is a critical yet challenging issue, and it has become even more difficult to secure assets as business use of technology has grown more complex. As a result, many companies will be assembling pieces of a security solution from different places, and that eventually may lead to a desire for thirdparty IT security solutions from an IT solutions provider or managed security services provider (MSSP).
Indeed, many organizations are opting for cloud-based managed security services rather than traditional on-premises systems. In fact, 62 percent of respondents use managed security services for initiatives like authentication, identity and access management, real-time monitoring and analytics and threat intelligence, according to PwC’s The Global State of Information Security Survey 2017, published in October 2016.
Regardless of the path chosen for upgrading your IT security, there are many different issues that must be addressed. The following questions will help guide your purchasing decisions. For your convenience, they are sorted by Products, People, Process and Policy – the four pillars of a strong IT security strategy (see related chart, Section 1, page X).
PRODUCTS
PEOPLE
PROCESS
POLICY
Read more about Cybersecurity.
Tags : Cybersecurity