
Cy·ber·se·cur·i·ty. The practice of being protected against the criminal or unauthorized use of electronic data, or the measures taken to achieve this.
At least, that’s what the dictionary says. Do you agree?
Over the years the term cybersecurity has been thrown around to the point where it is almost synonymous with terms like IT security or information security. It’s kind of like saying every square is a rectangle, but not every rectangle is a square.
Confused? Let’s break it down.
Every square IS a rectangle because a square is a quadrilateral with all four angles being right angles. Similarly, cybersecurity IS a part of the IT security umbrella, along with its counterparts, physical security and information security.
But not every rectangle is a square, since the criteria to qualify as a square means all sides must be the same length. The point is, not all IT security measures qualify as cybersecurity, as cybersecurity has its own distinct assets to protect.
CompTIA’s Chief Technology Evangelist, James Stanger says it best when he defines cybersecurity as “focusing on protecting electronic assets – including internet, WAN and LAN resources – used to store and transmit that information.”
Of course, the threat to these electronic assets are hackers who have malicious intent to steal proprietary data and information via data breaches. Thus, it would seem the fully realized definition should include an evolving set of cybersecurity tools designed to protect confidential data from unauthorized access. To do so, it’s necessary to consider how people, processes and technology all play equally important roles in keeping information safe.
One of the many advantages to living in a world where every device is connected is convenience. It’s incredibly easy to conduct work, manage your social calendar, shop and make appointments from your smartphone or device. That’s why it’s become second nature to many of us.
But, of course, the convenience of connected data also means threats from bad actors can do a lot of damage. Cybersecurity initiatives are essential to protecting our data and thus, our way of life.
Cybersecurity can be categorized into five distinct types:
To cover all of its bases, an organization should develop a comprehensive plan that includes not only these five types of cybersecurity, but also the three components that play active roles in a cybersecurity posture: people, processes and technology.
Let’s face it, no matter what precautions you put into place, if people don’t follow the rules, you’re still at risk. The saying “you’re only as strong as your weakest link” comes to mind. In most cases, human error is just that – a mistake.
Most people aren’t intentionally bypassing security protocol – they either aren’t trained to do so, or they aren’t educated about the significance of their actions. Conducting security awareness training and reinforcing the most basic cybersecurity principles with employees outside of the IT department can make a big difference in your company’s security posture.
Here are five ways the human factor can increase your cybersecurity risk:
When employees outside of the IT department are trained, IT pros can focus on process. The processes by which cybersecurity professionals go about protecting confidential data are multi-faceted. In short, these IT pros are tasked with detecting and identifying threats, protecting information and responding to incidents as well as recovering from them.
Putting processes into place not only ensures each of these buckets are being continuously monitored, but if cybersecurity attacks happen, referencing a well-documented process can save your company time, money and the trust of your most valuable asset – your customers.
The National Institute of Standards and Technology (NIST) under the U.S. Commerce Department has developed the Cybersecurity Framework for private-sector companies to use as a guide in creating their own best practices. The standards were compiled by NIST after former U.S. President Barack Obama signed an executive order in 2014. It’s a great resource to use as you work to combat your cybersecurity risk.
Once you have frameworks and processes in place, it’s time to think about the tools you have at your disposal to start implementation.
Technology has a dual meaning when it comes to your toolbox:
Back in the day, cybersecurity initiatives focused on defensive measures inside the boundaries of traditional tech. But today, policies like Bring Your Own Device (BYOD) have blurred those lines and handed hackers a much broader realm to penetrate. Remembering cybersecurity basics like locking all of your doors, windows, elevators and skylights will keep you from joining the cyber-crime statistics.
Staying ahead of cybersecurity threats isn’t an easy job. There’s a long list of threats that IT pros pay attention to, but the problem is that the list keeps growing. Today, cyberattacks happen on the regular. While some attacks are small and easily contained, others quickly spiral out of control and wreak havoc. All cyberattacks require immediate attention and resolution.
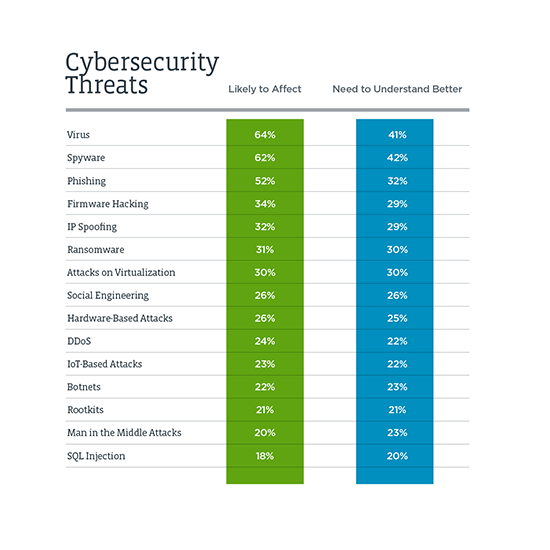
Here are a few common cybersecurity threats that fall into both categories.
Malware
Malware is software that has been created to intentionally cause damage. Commonly known as a virus (among other things), malware can cause harm simply by opening the wrong attachment or clicking on the wrong link.
Ransomware
Ransomware is actually a type of malware. The difference here is that ransomware infects a network or steals confidential data and then demands a ransom (typically currency of some sort) in exchange for access to your
systems.
Phishing Attacks
Phishing is just like it sounds. Hackers throw a line out there hoping that you’ll bite, and when you do, they steal sensitive information like passwords, credit card numbers and more. Phishing attacks usually
come in the form of emails that look legitimate and encourage you to reply.
Social Engineering
Social engineering involves malicious human interaction. This is a case of people outright lying and manipulating others to divulge personal information. Often, these people obtain information from social media
profiles and posts.
With the list of cybersecurity threats growing by the minute, it makes sense that the demand for cybersecurity jobs is rising as well. In fact, there are more than 300,000 cybersecurity jobs vacant in the United States.
According to CyberSeek – an online resource that provides detailed data about supply and demand in the cybersecurity job market – these are the top cybersecurity job titles.
Cybersecurity certifications assess the knowledge, skills and abilities that IT professionals have already mastered and reflect on what’s going on in the field today. The CompTIA Cybersecurity Career Pathway features four cybersecurity certifications and helps IT pros achieve cybersecurity mastery, from beginning to end:
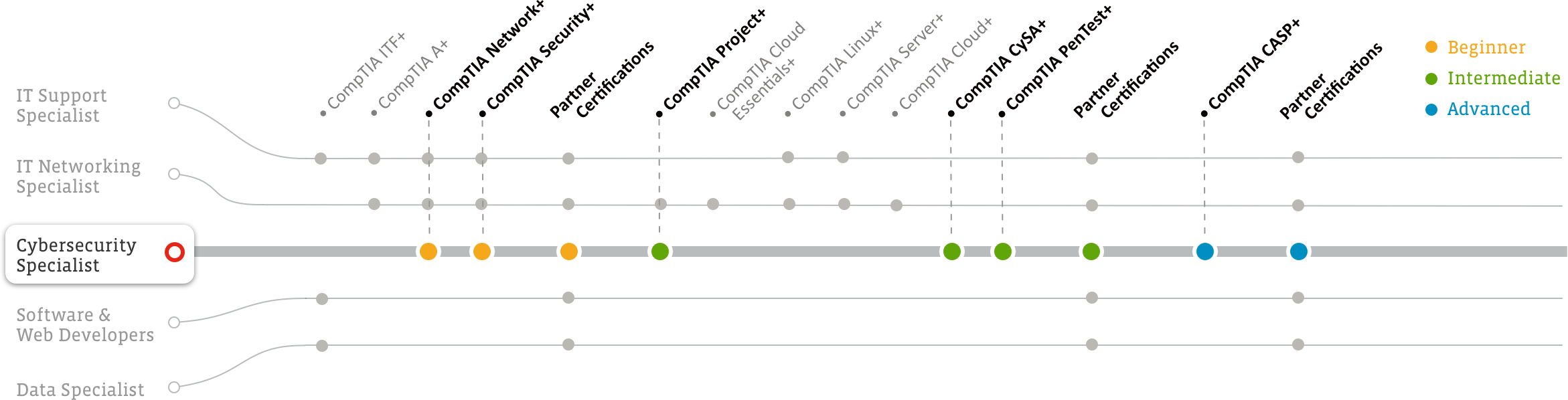
Learn more about how to get into cybersecurity (and other IT fields) on our career roadmap.
Organizations such as (ISC)2, ISACA, GIAC and Cisco also offer cybersecurity certifications. Other popular cybersecurity certifications include the following:
Businesses, governments and individuals store a whole lot of data on computers, networks and the cloud. A data breach can be devastating in a variety of ways for any of these entities.
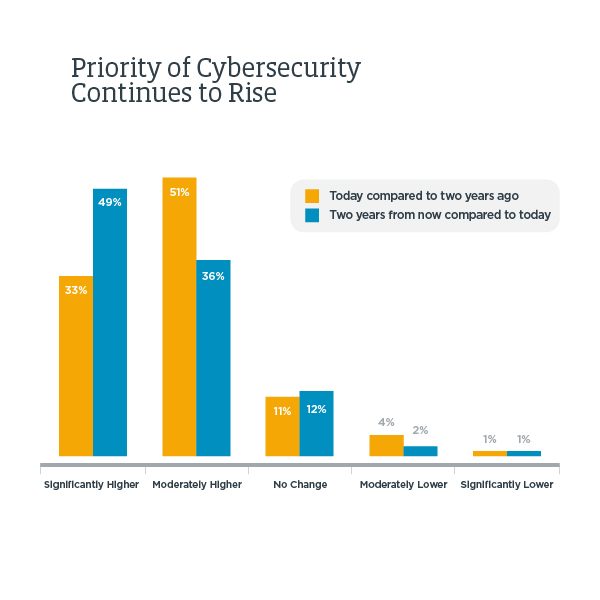
The good news is that the importance of cybersecurity has been steadily increasing over the years to the point where executives outside of the IT department are taking notice and setting priority. In fact, International Data Corporation (IDC) predicts that global spending on security will hit $103.1 billion in 2019, then grow at a compound annual growth rate of 9.2% through 2022, eventually reaching $133.8 billion.
The key takeaway? Cybersecurity is a complex practice, and the best way to prevent attacks and protect your information is via a multi-layered cybersecurity approach that weaves together your people, processes and technology.
Need more information? Check out the Future of Tech to learn more about the types of cybersecurity attacks, systems at risk and protecting digital assets.
Read more about Cybersecurity.
Tags : Cybersecurity