 Ask any conscientious IT executive today about cybersecurity and they’ll tell you it is an unrelenting task. To put it mildly, the checklist of daily duties and keep-you-up-at-night items is long and deeply challenging: Data and network protection efforts. Ransomware and business downtime avoidance. Compliance mandates. Employee education. You get the picture.
Ask any conscientious IT executive today about cybersecurity and they’ll tell you it is an unrelenting task. To put it mildly, the checklist of daily duties and keep-you-up-at-night items is long and deeply challenging: Data and network protection efforts. Ransomware and business downtime avoidance. Compliance mandates. Employee education. You get the picture.
Naturally then, another question to ask that IT executive is, “Do you need help?”. The answer for all but the most well-equipped—and confident—is often yes, and this is where solution providers, MSPs and tech consultants with cybersecurity expertise can find ample opportunity to offer their services.
Where specifically do companies need that cybersecurity help? As the recently published CompTIA State of Cybersecurity 2025 research makes clear, that need exists almost anywhere across an organization’s tech environment. For context, the research examines cybersecurity through the lens of the broad enterprise architecture model. Viewed this way, cybersecurity considerations manifest in every layer of an organization’s technology stack, from business operations planning and applications to data and individual cybersecurity products.
That’s a lot of places to plug in and provide value if you are an enterprising channel firm. As you can see in the following chart, a not-insignificant number of end customer firms turn to channel providers for assistance with their cybersecurity needs. These engagements often complement what a customer’s internal IT department is doing, or in some cases involve owning an entire IT function for the client, such as a help desk. In either case, cybersecurity expertise by the channel firm will be needed and expected.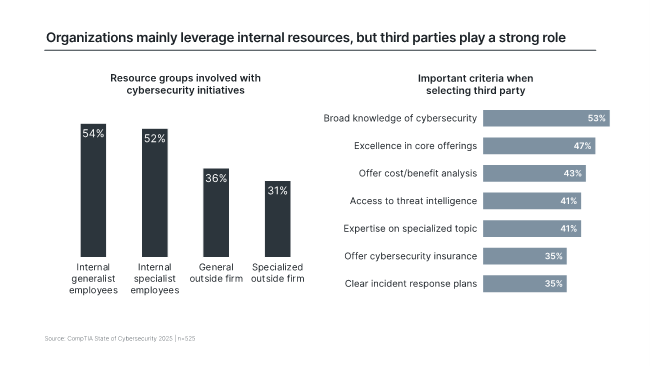
If you’re wondering how your firm can best capitalize on today’s cybersecurity opportunity, consider where your expertise and value proposition map to the individual layers of the enterprise architectural model below:
Business layer: This is all about helping customers set an agenda for cybersecurity priorities within their business/technology operations and making sure those priorities align with general business goals. For example, say a customer is looking to grow revenue through an aggressive outgoing marketing campaign that will result in capturing a massive amount of new customer data. Separately, you’ve helped that customer establish a cybersecurity priority that ensures the protection and privacy of all third-party data. Does the business goal of revenue growth via this marketing campaign align with the cybersecurity priority of customer data protection? Is there budget to spend to guarantee results? These are the types of consultative questions you can help answer at this layer in the model.
Application layer: This is a layer of the stack where you can help a customer define workflow between various applications and identify areas where potential vulnerabilities in the cybersecurity posture might exist. Risk assessment is a major opportunity in this bucket, especially as customers explore how and if they will incorporate AI and automation into their application workflow.
Data layer: This layer is all about securing data for your customers. Of all the pieces of the cybersecurity puzzle, data protection is likely the one that resonates most with customers. No one wants a breach, no one wants their private information exposed, etc. And it’s an area that is growing in opportunity for the channel to provide services such as conducting data audits, shoring up data infrastructure and selling and managing data security products. In the CompTIA State of the Channel 2024 report, a NET 72% of channel respondents identified data services as an area for revenue growth in the year ahead. Considering that cybersecurity services ranked even higher in terms of revenue projections in that same study, it’s a safe bet that expertise spanning both these areas will be in high demand.
Technology layer: This layer is the traditional wheelhouse for channel firms when it comes to cybersecurity. Product choices, whether that’s antivirus, firewall or other commercial software, represent the most tactical of all the cybersecurity moves a company must make. But it is not just about reselling products for a channel provider. Vetting the right solutions for customers, conducting integration and deployment work and providing ongoing management of the solutions, is a surefire way to generate greater profitability than comes from the initial product transaction.
Get more information.
Download CompTIA State of Cybersecurity 2025.

 Add CompTIA to your favorite RSS reader
Add CompTIA to your favorite RSS reader

